
BLOG

BLOG
When it comes to security, it’s not always the advanced and complex techniques that matter. At times, even the simplest of the practices can do wonders for the security of your applications. Using tools like SonarQube and Appknox in the DevOps pipeline for a thorough code analysis is one such practice.
Despite its advanced capabilities as a code review tool, SonarQube has its own limitations and weak points. And as the leading SAST (Static Application Security Testing) solution in the market, Appknox has the ability to deal with those limitations and take application security to a whole different level. Let’s see how.
Table of ContentWhat are the Features of SonarQube? Difference between Source Code and Binary Code Analysis? |
Static Application Security Testing or SAST is one of the most versatile techniques through which source code analysis is done. It further plays a vital role in assisting developers to identify security vulnerabilities within the early stages of development. This results in resolving issues quickly without having to disrupt development cycles or pass on subsequent threats to upcoming stages of development, that too before resolution.
A unique white box testing approach is used in SAST where source code is assessed by the tester in order to discover security vulnerabilities that are present in the application’s source code. SAST makes finding errors in non-compiled codes easier. These include math errors, syntax errors, insecure or invalid references, etc. Binary and byte-code analyzers can be used for running SAST smoothly.
One of the best features of SAST is that it doesn’t necessarily require the presence of code execution beforehand or functional applications of any kind and is executed quite early in the Software Development Life Cycle (SDLC).
Used frequently for analyzing source code quality, Sonar or SonarQube is an open-source platform based on web protocols. More than 20 different kinds of programming languages can be analyzed and managed through SonarQube plugins. These plugins further help in detecting vulnerabilities and enhancing the functionalities of source codes.
Languages such as Python, JavaScript, Groovy, Flex, PHP, Java (including Android), PL/SQL, COBOL, Swift, etc. are supported by SonarQube.
Detecting security vulnerabilities, providing succinct reports on coding standards, code complexity, comments, bugs, duplicated code, etc. are some of the other facilities provided by SonarQube.
Being a leading resource for code analysis, SonarQube offers several eye-catching features. Some of them include:
One of the most basic features of SonarQube is that it can work with 20+ different languages which include Java, .NET, JavaScript, COBOL, PHP, Python, C++, Ruby, Kotlin, and Scala.
Tricky bugs or pieces of code that can bring faults into the system can be detected easily by SonarQube.
Code smells are those vulnerabilities that indicate that there might be a problem with the code in the future. SonarQube is also efficient at detecting code smells.
Security issues that can damage the system interface are detected by SonarQube. For Instance, if some developer forgets details such as username, password, etc. which have directly been written in the code or how to close and open an SQL database, then SonarQube plays a massive role in identifying these loopholes.
Projects which are diverse and specific in terms of utilization can be created easily with the help of SonarQube and are known as Quality profiles.
Detecting the presence of tricky bugs in the execution paths is one of the most important features of SonarQube. Once integrated with Jenkins or some similar deployment tool, SonarQube starts working by itself and detects severe bugs and errors in its pathway.
Automation of SonarQube can be intensified with the help of integration or deployment tools. This process helps SonarQube in detecting errors in the background and handling technical concerns and code smells singlehandedly.
You can easily integrate SonarQube with a version control software of your choice. This plays a very important role in identifying errors and vulnerabilities in the version of the code you are proceeded towards.
SonarQube plays a very important role in detecting memory leaks in your application systems if the tendency of the application surges towards failure or running out of memory.
SonarQube comes with a diverse set of plugins known as “SonarLint” which massively supports the integration of its software with an IDE.
This also means that you don’t need to install the whole SonarQube package.

Being the primary pillars of security testing, binary and source code analysis have their own pros and cons. Let’s take a look at the key differences between them.
● Scope: Binary analysis covers the whole application including the Libraries, Frameworks, and SDKs. Source code analysis, on the other hand, is limited to the visible source packages and might miss vulnerabilities in the compiled code.
● False Positives/Negative: Less false positives/negatives are detected in the binary analysis as compared to the source code analysis as the dead/unused code is removed by the compiler.
● Detection of Runtime Issues: Along with DAST, binary analysis can help detect runtime issues and logical bugs which are not detected by source code analysis.
● Speed of Execution: When it comes to speed and accuracy of execution, binary code analysis is generally faster and accurate than source code analysis.
With SonarQube plugins, we can perform a complete automated analysis. SonarQube plugins are available for several continuous integration tools such as Jenkins, Hudson, Atlassian Bamboo, etc. along with Maven, Ant, Gradle, and MS Build.
With the help of SonarLint plugins and several external tools such as Active Directory, GitHub, and LDAP, SonarQube is able to integrate with the developmental environments of Visual Studio, IntelliJ IDEA, and Eclipse.
We saw how versatile SonarQube is when it comes to code analysis. But, it has its own weaknesses and Appknox plays a very important role in handling them. These include:
● No. of Users: Appknox lets an unlimited number of users use the service.
● Quality of Report: Appknox provides the best in the class report after testing and that too with a complete drill-down of all the vulnerabilities.
Below screenshot is the review from one of our customers on Gartner.
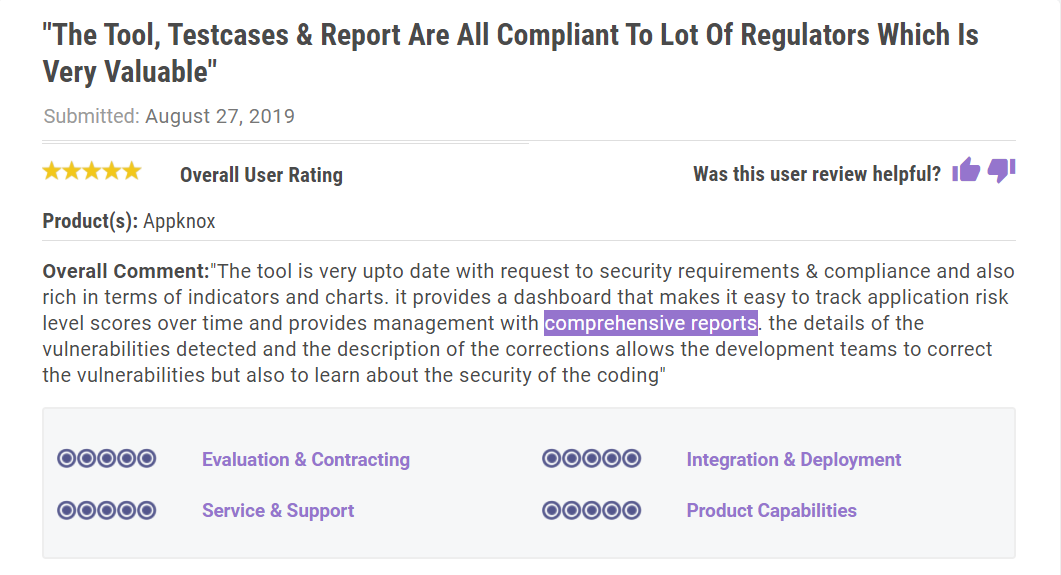
● Better Support: We provide users with all the assistance required during deployment, bug fixing, and security enhancement.
● Remediation: With Appknox, users also get calls for remediation so that the after-effects of the applied mitigation strategies could also be assessed.
● Swift Service: We get back to our customers with a complete vulnerability audit within 30 mins of call.
● False Positives: Appknox massively reduces the number of false positives as compared to SonarQube.
Apart from these improvements, Appknox also aids its users with:
● An improved Search Functionality
● Removal of issues that overlap with SonarQube and Appknox
● Risk segregation based on their vulnerability level along with score
SonarQube is widely loved across the security testing landscape because of its enriching capabilities like better integration, language support, and other exciting security features. However, it also poses challenges on several fronts like setup, navigation, and quality of the analysis. Appknox efficiently deals with these limitations of SonarQube and helps enhance the security of your applications.

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
