BLOG

BLOG
In a world where software tools are spawning businesses each day, and cyberattacks and threats are increasing rapidly, ensuring the clarity and security of these tools has become a top priority.
Regulators suggest new tools and standards to ease the complexities in a software supply chain. One such tool is the Software Bill of Materials (SBOM). It lists all the components used in building the software and helps identify areas for improvement.
SBOMs have numerous applications, especially in ongoing vulnerability testing, governance, and Incident Response. Security teams can leverage SBOMs to their fullest potential to strengthen their incident response efforts.
It is a fact that SBOM helps to maintain an inventory of every software constituent, but for it to prevent malicious attacks, security teams need to make plans to operationalize it.
This blog focuses on how to scale and operationalize SBOM for incident response. It is also a nexus for a broader set of considerations when choosing an SBOM tool. But first, let’s cover the foundational knowledge of SBOMs and how they help in Incident Response.
An SBOM is a comprehensive list of components used to build a software solution, including frameworks and libraries (third-party & open source) and the dependencies of these components on each other. It also provides baseline information such as supplier name, versions of each component, their vendors, licensing and copyright details, and known vulnerabilities connected with these components.
By giving comprehensive visibility into the software constituents, SBOM helps organizations identify components with potential supply chain security or license risks and apply patches or updates when identifying vulnerabilities.
A complete SBOM can greatly assist Incident Response (IR) teams in comprehending the inner workings of an application or API, ultimately providing valuable context for addressing an attack. Additionally, SBOMs can aid in identifying the repositories and individuals associated with a project, ultimately expediting the response time.
Incident Response (IR) refers to the structured processes and technologies an organization implements to detect and respond to cyberattacks, threats, breaches, and other security incidents. It involves coordinated steps to identify, analyze, mitigate, and recover from a cyberattack compromising data and its integrity, availability, and confidentiality.
SBOMs play a crucial role in incident response for mobile app security, similar to how a detailed blueprint guides construction workers during a building emergency. Just as the blueprint provides a clear layout of the building's structure, SBOMs offer a comprehensive inventory of all software components and their dependencies within the mobile app. When a security incident occurs, incident response teams can swiftly refer to the SBOM to identify vulnerable components, assess the impact, and take targeted remedial actions.
The prima facie objective of IR is to prevent these attacks before they happen. However, IR extends to minimizing the cost and level of business disruption after an attack as well.
Now, let’s discover the top-five strategies to efficiently integrate SBOMs into incident response workflows and unlock their potential in bolstering overall mobile app security.
SBOM and Incident Response are closely interconnected. SBOM helps in detecting incidents by providing the inventory of software components.
Security teams can compare these listed components against known vulnerabilities and identify potential threats and incidents. Additionally, SBOM lets them analyze these vulnerabilities and helps identify patterns and recurring issues. It further allows organizations to improve their IR strategies for future incidents.
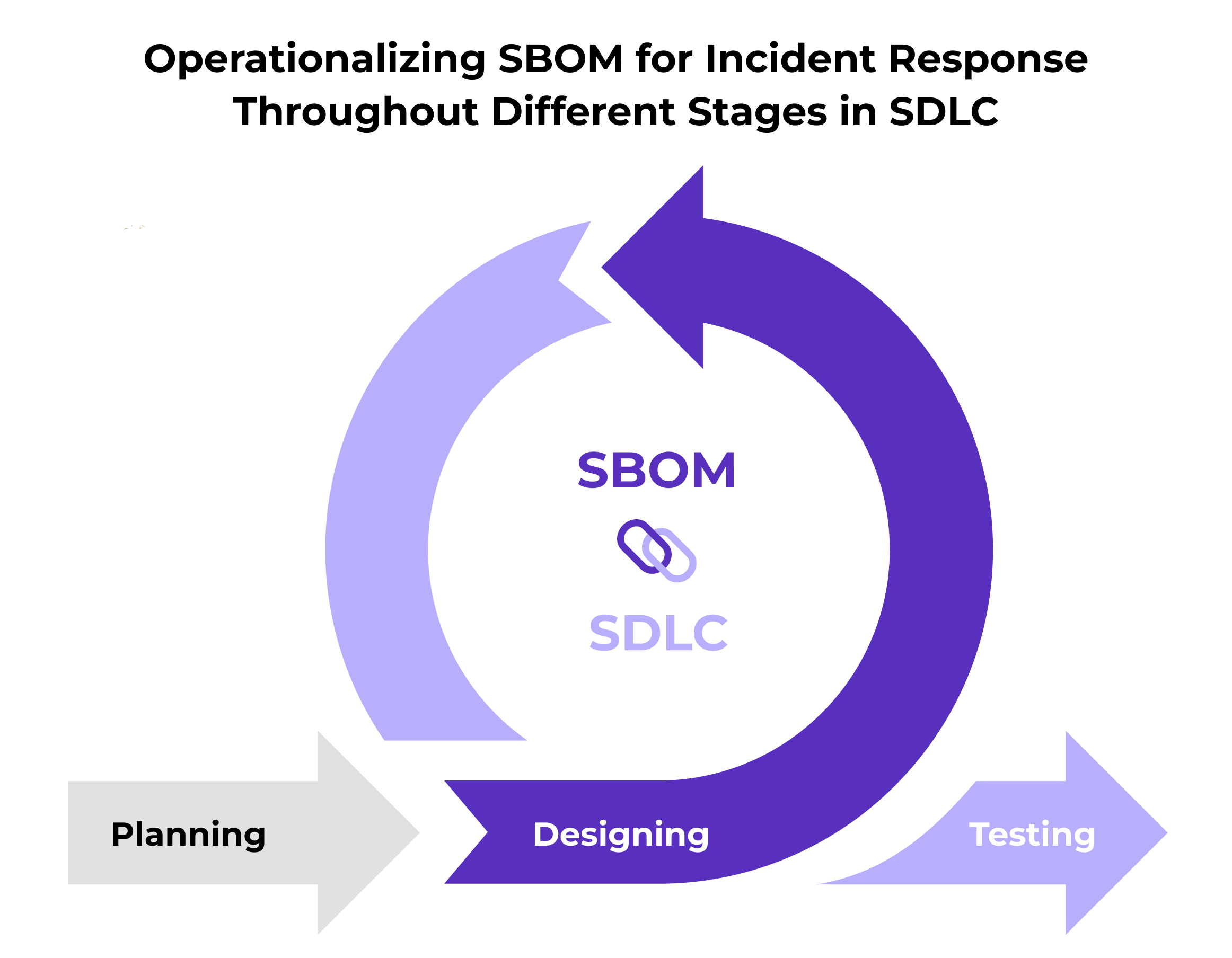
Here's how Incident Response teams can operationalize and integrate SBOM practices throughout different stages in Software Development Life Cycle (SDLC)-
During the planning stage, gather the information to decide what goes into the software, including the features, definitions, and acceptance criteria. Creating an SBOM, this stage can help development teams ensure each component and the corresponding details are included right from the beginning, provided a reliable SBOM tool is in place.
However, don’t rely solely on first-party SBOM solutions. Consider third-party SBOM tools as well since software supply chains are quite complex and often involve the use of components crafted by third-party companies.
Pro tip: To choose the right SBOM solution, make sure you know which SBOM format and specifications (Cyclone DX or SPDX) you want to use. Also, be clear on how you want to deliver the SBOMs (during a release or as a part of the build process).
It is the stage where engineering and software development teams work in tandem to build the software.
Imagine you spend months building software that depends upon a particular open-source component. After the build process, you discover that some license issues render the component unusable.
Hence, getting your SBOMs generated during the designing and building stages is crucial. Because if you can run an SBOM report after every build, you'll get complete component information, such as the version strings and license, and also know whether the component has any known vulnerabilities associated with it.
Incorporating SBOMs (whether first-party or third-party) into the software testing phase is the smartest thing you can do. It will help you assess security risks and vulnerabilities in the software components and take necessary corrective actions.
It will include identifying which risk to address first, which to leave until the next version or patch, and alerting your vendors about the vulnerability. It will also help you comply with service level agreements your organization has in place.
One effective strategy to streamline SBOM generation is automation. By integrating SBOM generation into the CI/CD pipeline through tools like Jenkins or GitLab CI/CD, the process becomes seamless and continuous. Automation ensures accurate and up-to-date SBOMs, reducing the risk of manual errors and saving valuable development time.
Establish a centralized repository to store and manage all SBOMs. This repository should be easily accessible to your incident response and development teams.
|
Enhance Security with Appknox SBOM By utilizing Appknox's binary-based approach, app developers and security teams can safeguard their mobile applications from the risk posed by using untrustworthy and insecure third party libraries or open source components. |
A well-thought-out strategy involves integrating SBOMs into the incident response planning process. Define clear procedures for analyzing SBOM data during security incidents and assign dedicated personnel, such as security team leaders, to oversee the process. Embed SBOM analysis guidelines in the incident response playbook to enable swift identification and assessment of impacted software components.
Real-time SBOM analysis is a key strategy to expedite incident response. Utilize tools like OWASP Dependency-Check or Appknox SBOM to quickly identify affected software components and their dependencies during security incidents. Rapid analysis aids in accurately assessing the impact and enables teams to respond promptly with appropriate measures.
.png?width=2324&height=1300&name=Factors%20to%20Choose%20SBOM%20For%20Incident%20Response%20(2).png)
Here are a few factors to consider while choosing SBOMs for Incident Response-
SBOM should provide complete, accurate, and up-to-date information by listing all the components and dependencies used in your software applications. It should also include details about their licenses and versions. Additionally, ensure that the SBOM you choose supports the programming languages used in your organization.
SBOM should be compatible with your software deployment framework. It should be able to integrate smoothly with existing development tools, including vulnerability scanning tools and SDLC tools, vulnerability databases, CI/CD pipelines, and DevOps tools.
It should have a user-friendly interface so the security teams and developers can easily access, understand and use the information provided. It will help them make the most of the tool and detect vulnerabilities without any hassle.
The SBOM tool you choose must handle the complexity involved in your software applications. It should also be scalable enough to meet the growing needs of your organization.
It should have strong security policies and comply with all relevant data privacy regulations. The underlying objective is to choose an SBOM that ensures the protection and confidentiality of the sensitive software information it collects and stores.
It should also identify and track open-source licenses employed in the software to ensure that your organization complies with the terms and conditions of those licenses.
Choose the SBOM that offers the best services, features, and capabilities at the most affordable price.
Select an SBOM tool that ensures round-the-clock monitoring for potential vulnerabilities in all of your organization's software components.
Your SBOM tool should provide good customer support. It should be empowered by an agile and responsive support staff that can help you with technical issues and queries. While some SBOMs also offer ticket-based support for more complex issues, others offer a dedicated support package for custom implementation.
Since SBOMs are very detailed and lengthy, you should have the right tools to operationalize them. And once you choose the right SBOM tool, you must couple it with a robust SBOM Management Platform to realize its full potential.
For instance, Appknox's SBOM will help you understand the entire attack surface of the application & prioritize remediation, including:
SBOMs assist organizations across the globe with improved application security, precise threat location detection, faster issue resolution, and reduced business risks- all while complying with legal and regulatory requirements and industry standards.
Use this blog guide to select the most suitable SBOM tool and operationalize it to build a robust security infrastructure that detects and mitigates probable threats before they happen.
Reach out to us now for a complimentary consultation.
To ensure the accuracy and completeness of SBOMs, implement automated SBOM generation tools such as Appknox, which minimize human error. Regularly validate SBOM data against the actual software components used in the app to identify any discrepancies. Conduct periodic audits and manual reviews of SBOMs to verify their accuracy.
Encourage developers to proactively update SBOMs with each code change. Maintain a version-controlled centralized SBOM repository, ideally using Git, to ensure version tracking and easy access for verification.
While SBOM generation significantly enhances security, it also poses potential risks. If using source code-based SBOM generation, exposing sensitive code during the process can lead to code theft or unauthorized access. To mitigate this risk, adopt binary-based models like Appknox that extract SBOM data without requiring the app's source code.
While most countries have no regulations that mandate the use of SBOM, there is an exception. For instance, in 2021, the Biden Government released an executive order. According to this order, any organization selling software to the federal government must facilitate an SBOM.
You can also check NITA’s list of minimum elements required for creating SBOMs. Although not mandatory everywhere, creating an SBOM does enhance your security stature.
With the advent of digitalization and advanced technology, software tools have become an integral part of every organization. Therefore, an organization concerned about its security infrastructure and wanting to identify and mitigate potential vulnerabilities and threats before they are exploited should employ SBOMs.
SBOMs provide insights into the required regulatory and licensing requirements. It will allow you to ensure that you procure every required license and adhere to the terms and conditions. This may entail paying unexpected licensing fees but will help you avoid fines, lawsuits, and penalties. Hence, the cost saved overrides the cost incurred.
Measuring the effectiveness of SBOM implementation involves various metrics that provide insights into its impact on mobile app security. Key metrics include:
1. SBOM Coverage: The percentage of software components accurately listed in the SBOM reflects its completeness. Higher coverage indicates better visibility into the app's supply chain, reducing blind spots.

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
