Secure by design.
Adhere to global security compliance standards, effortlessly.
Appknox is designed to help you meet security compliances and gold data privacy standards.

Simplifying compliance, one standard at a time
Simplify compliance management
Dealing with multiple regulatory standards can be overwhelming. Appknox streamlines this by centralizing compliance on the platform and lets you focus on strategy, not paperwork.
Strengthen data security
Data breaches are a constant threat. Appknox helps you proactively shield the sensitive information in your apps, ensuring your data and reputation stay intact.
Ensure continuous compliance
Regulations evolve and Appknox keeps you ahead, flagging vulnerabilities that don’t align with the latest standards so you mitigate those effortlessly.
Get actionable insights on complying with industry-specific regulations,
international and local security, and data privacy standards
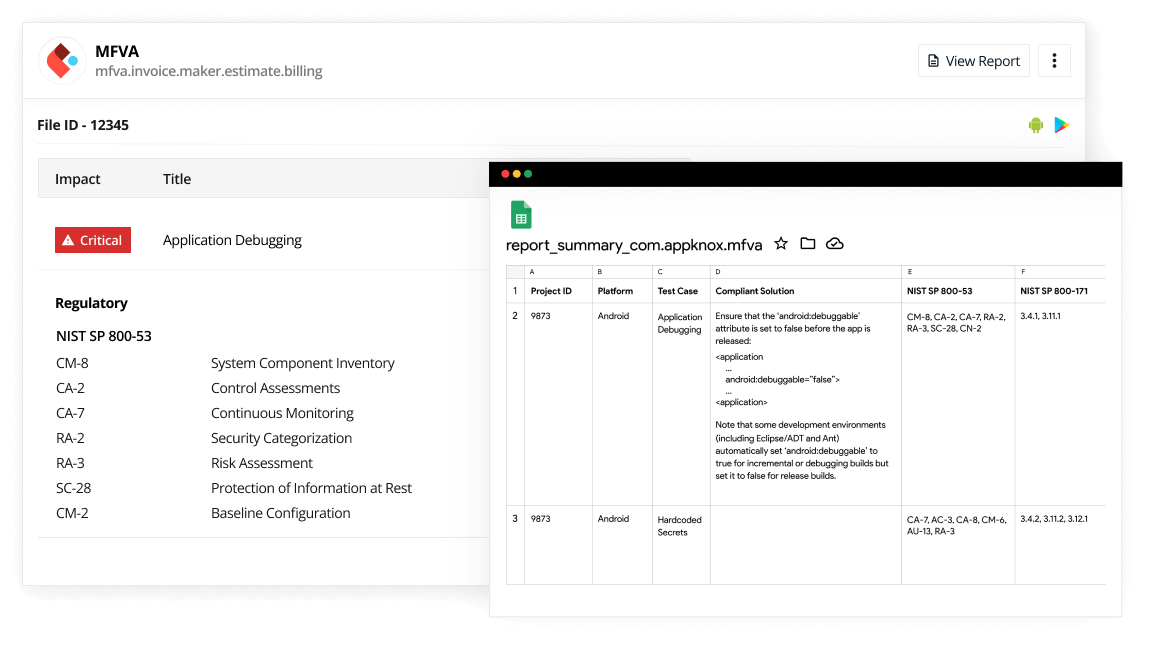
Check if the vulnerabilities detected violate any compliance on the Appknox
platform or download the report in your preferred format.
Robust security with compliances flagging
Appknox is built to achieve compliance with leading information security standards. Ensure your applications meet rigorous security requirements across various regulations.
.png?width=88&height=88&name=General%20Data%20Protection%20Regulation%20(GDPR).png)
General Data Protection Regulation (GDPR)
Geography
European Union (EU)
Mandated for
Organizations processing the personal data of EU citizens.
Description
Ensure GDPR compliance with Appknox designed to help you safeguard personal data. Protect EU citizen data and align your applications in line with the strictest GDPR requirements.
Payment Card Industry Data Security Standard (PCI-DSS)
Geography
Global
Mandated for
Organizations that store, process, or transmit payment card information.
Description
Meet PCI-DSS standards effortlessly with Appknox. Secure payment card data, minimize fraud risks, and maintain your customers' trust by relying on Appknox to flag any inconsistencies.
.png?width=89&height=90&name=Health%20Insurance%20Portability%20and%20Accountability%20Act%20(HIPAA).png)
Health Insurance Portability and Accountability Act (HIPAA)
Geography
United States
Mandated for
Healthcare providers, health plans, and organizations handling protected health information (PHI) in the U.S.
Description
Safeguard PHI and ensure HIPAA compliance with Appknox. Protect patient data with Appknox timely alerts and keep your applications in strict adherence to HIPAA requirements.
.png?width=88&height=88&name=National%20Institute%20of%20Standards%20and%20Technology%20(NIST).png)
National Institute of Standards and Technology (NIST)
Geography
United States (Primarily), Global (As a best practice)
Mandated for
U.S. federal agencies
Description
Align with the NIST cybersecurity framework using Appknox. Manage risks, and secure your mobile applications with Appknox's advanced compliance tools.
.png?width=88&height=88&name=Common%20Weakness%20Enumeration%20(CWE).png)
Common Weakness Enumeration (CWE)
Geography
Saudi Arabia
Mandated for
Global
Description
Identify and eliminate vulnerabilities with Appknox as it thoroughly tests and analyzes your mobile applications, flagging CWE-listed weaknesses effectively.
Payment Card Industry Data Security Standard (PCI-DSS)
Geography
European Union (EU)
Mandated for
Organizations that store, process, or transmit payment card information.
Description
Ensure GDPR compliance with Appknox designed to help you safeguard personal data. Protect EU citizen data and align your applications in line with the strictest GDPR requirements.
OWASP compliances
Appknox is built to help enterprises comply with the most comprehensive OWASP standards.
OWASP Mobile Top 10 2024
Secure your mobile applications with Appknox’s tools, built to detect and address critical risks from the OWASP Mobile Top 10 2024. Safeguard against the latest mobile security threats today.
OWASP API Top 10 2023
Manage API vulnerabilities effectively with Appknox as it identifies and mitigates risks from the OWASP API Top 10 2023, securing your APIs against potential threats.
Mobile Application Security Verification Standard (MASVS)
Ensure your mobile applications meet MASVS requirements with Appknox. Get actionable reports and address crucial security aspects.
Mobile Security Testing Guide (MSTG)
Leverage Appknox to implement MSTG principles and conduct comprehensive security tests. Identify and resolve vulnerabilities with precision, following the latest security guidelines
Say yes to proactive compliance detection
Appknox actively flags vulnerabilities that may breach any OWASP-mandated compliance standard. Stay ahead of potential issues and maintain compliance effortlessly.

We’ve put together the ultimate actionable MASVS compliance checklist for security teams.
More on compliance with Appknox
Compliances demystified with in-depth resources.
Gartner hype cycle for application security 2023
Gartner Hype Cycle for 2023 assesses the levels of maturity, adoption, and societal effects...
Know more ▶Guide to API security testing: Software & trends
Application Programming Interface (APIs) have been around for a long time. Their widespread...
Know more ▶