-1.png?width=623&height=467&name=A%20Guide%20to%20building%20secure%20government%20apps%20(10-Step%20approach)-1.png)
Guides
A guide to building secure government apps (a 10-Step approach)
About a decade ago, most government applications and websites lagged behind their contemporaries in terms of design, user experience, features, and whatnot.
This was probably because most government organizations were reluctant to embrace new technologies in the past. The reason could have been the increased service cost, implementation challenges for wider mass, or anything else.
Governments have access to sensitive information on millions of citizens, military, defense, finance, and more. If not protected, the whole country, state, or region can suffer devastating consequences. Hence, they are responsible for securing such data to prevent cyberattacks, data theft, financial loss, and other security issues.
With rampant cyberattacks sparing no industry or geography, governments have begun realizing the advantages of implementing security technologies in their apps and sites.
According to Statista, the global market for government software was valued at US$ 16.5 billion in 2020 and is expected to grow at 1.5% by 2025.
So, when you create an app for the government, focus on implementing advanced security strategies. Follow the below steps to proceed with secure app development:
Table of content
- Introduction
- 01. Understand the Industry Specific Threats
- 02. Conduct a Risk Assessment
- 03. Use Encryption
- 04. Implement Strong Authentication & Access Controls
- 05. Keep Software Up to Date & Patched
- 06. Regularly Test and Monitor Security
- 07. Train Users
- 08. Compliance with Regulations
- 09. Use Secure Communication Protocols
- 10. Have an Incident Response Plan
- Conclusion
Government apps and finance apps are the favorite targets of cyber criminals, as reported by the FBI. This statement has its value of truth in any country or state which is why if there are apps or websites that need the most security, they are none other than government apps.
You can ensure the security of your government app by following the ten steps outlined below.
01. Understand the Industry Specific Threats
The first step in building secure government apps is to understand the types of threats that they may face. Government apps or websites can also be further categorized into transportation, documentation, taxation, and many more.
Every category of the app has its own threats which needs to be specifically taken care of. Some examples are:
1. Healthcare: Ransomware attacks on hospitals and healthcare providers, patient data theft, and digital medical equipment embezzlement.
2. Retail: Credit card fraud, customer data theft, Point of sale (POS) system attacks, and supply chain disruptions.
3. Finance: Phishing scams aimed at bank customers, financial information theft, and denial of service attacks against financial institutions.
4. Energy: Cyber attacks on power grids and oil and gas infrastructure, physical facility sabotage, and intellectual property theft.
Be it any industry, the biggest threat for any govt sub-unit would be cyber espionage which allows unauthorized access or exfiltration of sensitive information by a foreign government or organization.
It is important to keep in mind that both nation-state actors and cybercriminals may target government apps and that the types of information stored in these apps may be highly sensitive.
02. Conduct a Risk Assessment
This is one of the practical steps in understanding the threats. Before beginning development, conduct a thorough risk assessment to identify potential vulnerabilities and threats.

This assessment should consider the types of information that will be stored in the app, as well as the potential impact of a security breach. Here’s a quick general How to conduct a Risk Assessment for your Mobile App:
a. Determine which assets and systems must be safeguarded: Identify the organization's critical assets and systems, such as data, networks, hardware, and personnel.
b. Identify potential threats and vulnerabilities: Identify potential threats and vulnerabilities, such as natural disasters, cyber-attacks, or human error, that could potentially harm the organization.
c. Determine the threat's likelihood and impact: Evaluate the probability and potential impact of each identified threat. This will aid in prioritizing which threats to address first.
d. Examine the current controls and security measures: Assess whether the current security measures and controls are adequate to protect against the identified threats.
e. Develop a risk management plan: Based on the assessment results, your plan should include strategies and actions to mitigate or manage the identified risks.
f. Implement the risk management plan: Put in place the identified risk-mitigation and risk-management strategies and actions.
g. Monitor and review: Frequently monitor and review the impact of the risk management plan, and make updates as considered necessary.
03. Use Encryption
Encryption is a key component of protecting sensitive information stored in government apps. Data should be encrypted both at rest and in transit to prevent unauthorized access.
Various algorithms and protocols are working on the internet these days to make the exchange of confidential information secure. Messaging applications do implement encryption, but not each one of them makes the encryption end-to-end.
1. Need for End-to-End Encryption
The answer is simple - to make the user’s private information hidden from any third-party user. This may be the rival state government, hackers or any other intelligence agency.
The service provider may or may not allow third parties like the government to access the data as in the case of any criminals or terrorist activities.
But what if the servers get hacked? The information might then be in the wrong hands. In such cases, the users prefer to choose end-to-end encryption, where even the service provider cannot access decrypted data.
2. Methods that existing messaging applications are using
While many applications mention that they implement end-to-end encryption, only a few of them prove to do so.
There is a very famous application that we can’t name here, but it provides an optional feature of Secret chats using a protocol named “MTProto.”
This means that not even the server can decrypt our messages. Additionally, encryption keys should be securely managed to prevent unauthorized access.
3. Few Algorithms To Encrypt Government Apps
a. Diffi-Hellman Key Exchange Algorithm
Today we will be discussing the Signal Protocol in detail. But before that, we need to be aware of the Diffie-Hellman key exchange mechanism.
With simple encryption, the messages are usually encrypted only between the users and the server, making use of some cryptographic keys, hence making data vulnerable on the server.
We want these keys only to exist between the users and not the server. But how is this possible? Suppose we have two Clients - Alice and Bob.
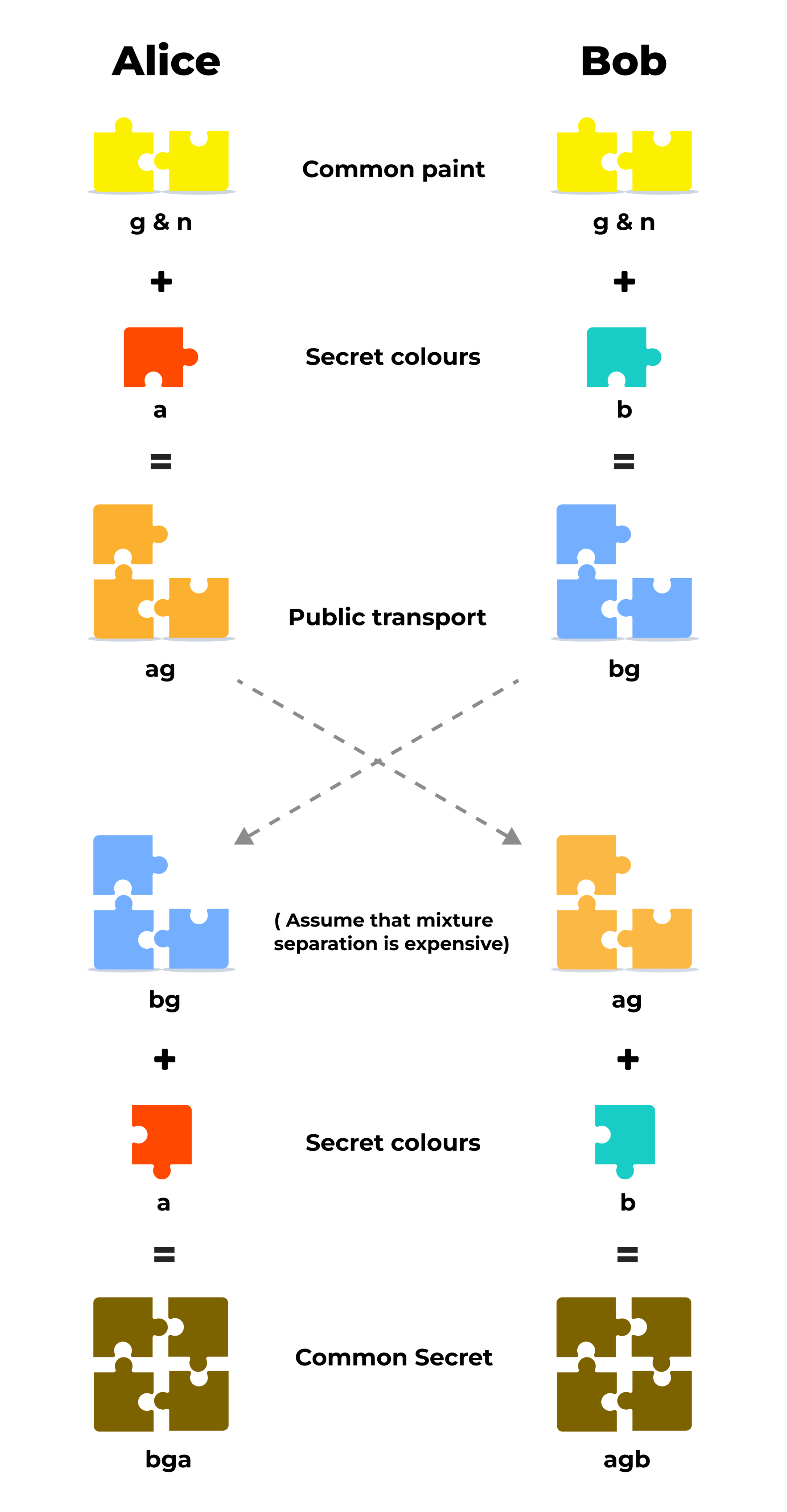
- Alice and Bob agree to use two common prime numbers (g & n) provided by the server.
- Now, these are combined using some mathematical calculations with the Private keys of Alice and Bob => a + g = ag and b + g = bg.
- We exchange these Ephemeral / Public Keys ag and bg via server.
- Combine the exchanged keys with the Private keys of Alice and Bob respectively to form a Shared Secret Key => ag+b = agb and bg+a = bga at both ends.
- Now the attacker might be aware of g, n, ag & bg as these are being shared publicly, but not a & b since these are private keys only available to Alice and Bob.
- It is too difficult for any intruder to split up the public components ag and bg.
- Any attacker can combine ag+bg = abgg (extra bit) - too hard to figure out.
Whitfield Diffie and Martin Hellman developed this mechanism to derive the cryptographic keys instead of exchanging them completely in public.
It is explained using colors; since it is not possible to separate colors once mixed, similarly, it is hard to figure out the secret keys using only the public components once combined mathematically with the prime numbers provided by the server.
b. Double Ratchet Mechanism
Why Double Ratchet? We got end-to-end encryption using, now, why does the Signal protocol still need another algorithm?
When a user is offline, it gives an attacker a lot of time to find and use public keys available on the server. Since the key is always the same for a long period, it makes the messages vulnerable. You need to update the keys regularly!
In messaging applications like Signal and Whatsapp, these keys are updated for every message. For implementing this, the Double Ratchet algorithm came into play.
A ratchet function is a function that can turn one way only, i.e. it cannot move backward. What we will be using here is called a KDF Ratchet, since you cannot go back to figure out what the key was.
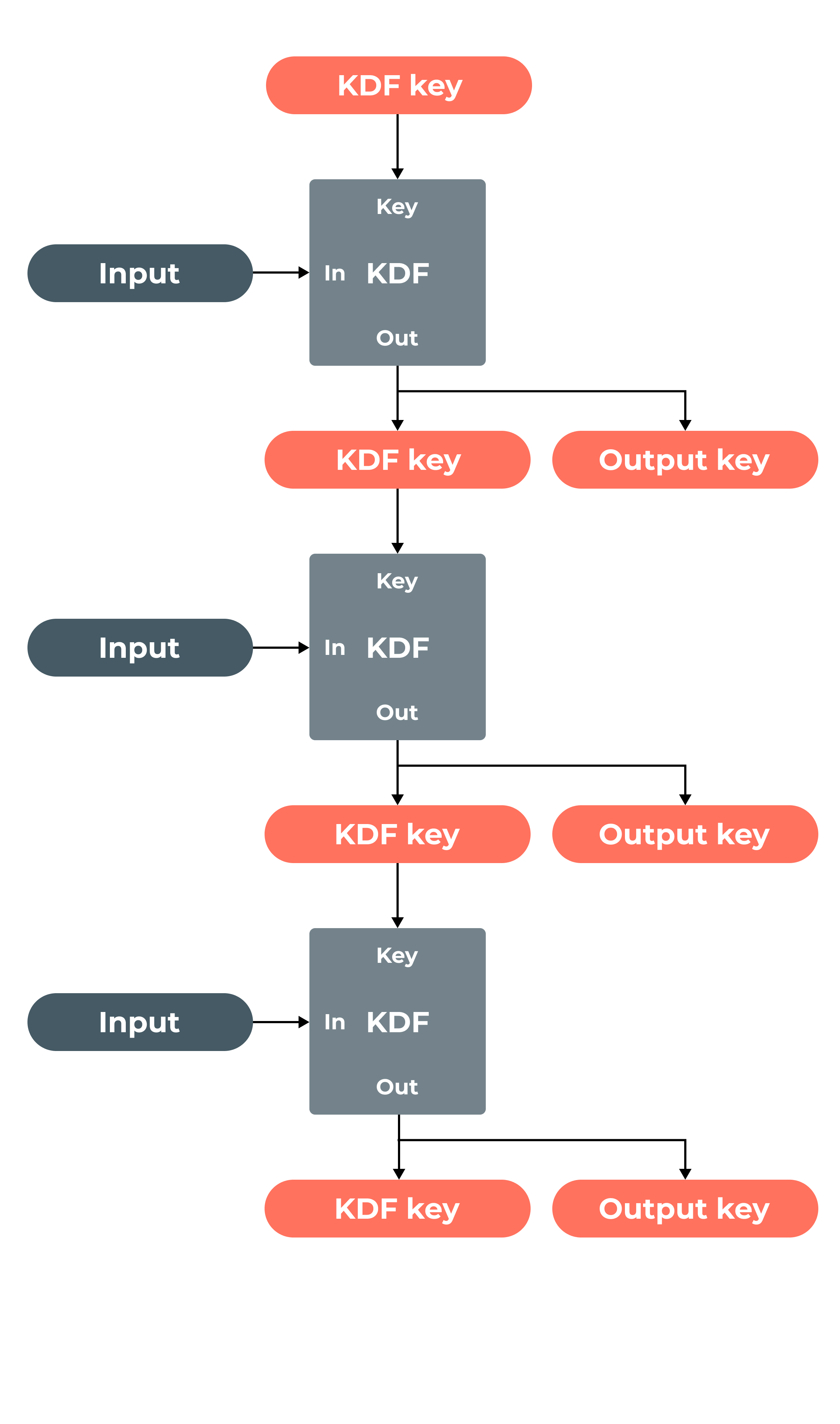
This function works as follows-
A KDF key and some input data are taken as input to the KDF Ratchet function.This function generates an output key for data and another key for the next KDF Ratchet as input.
This creates a KDF chain, as presented in the diagram below, with three inputs being processed and producing three output keys.
- If the attacker gets one key, he/she will not be able to undo the operation performed by KDF Ratchet to figure out the input data, but he/she will only be able to access future messages. That’s a huge problem! To ensure future secrecy, we use a Diffie-Hellman Ratchet with the KDF Ratchet function of Alice and Bob, forming a Double Ratchet.
- In such a session, we have three chains on both ends, i.e., a Root chain, Sending chain, and Receiving chain. The sending chain of Alice is synchronized with the receiving chain of Bob and vice versa. These start at the same time.
In case of any asynchronous event like non - receival of messages or delay or misuse of keys, the receiver keeps a check on the key, which is not deleted until all messages are received.
04. Implement Strong Authentication & Access Controls
Although providing an app with secure algorithms already drops the risk factors significantly, we can still reduce the risk factors to a bare minimum by implementing strong authentication.
Implementing strong authentication and access controls is critical for preventing unauthorized access to government apps. To ensure that only authorized users can access the app, use role-based access controls and implement strong passwords in conjunction with multi-factor authentication methods such as a password and fingerprint or facial recognition.
05. Keep Software Up to Date & Patched
This is basically a post-development process still a very important aspect of securing app. Attackers can exploit software vulnerabilities to gain unauthorized access to government apps.
It is important to keep all software, including the app itself and any underlying infrastructure, up to date to address known vulnerabilities.
How you can do it? By following these best practices-
1. Enable automatic updates
2. Monitor for updates
3. Test updates before deployment
4. Keep track of updates
06. Regularly Test and Monitor Security
Regularly testing and monitoring security measures can help to identify and address potential vulnerabilities. To ensure regular testing of your app for security, the following information can help you:
1. Penetration Testing (PT): Ethical hackers or skilled security researchers can mimic an attack to surface your government app's vulnerabilities.
2. Vulnerability Scanning: It automatically scans the app and its infrastructure to look for vulnerabilities. Automated SAST, DAST, and API testing can help with a quick Vulnerability Assessment (VA) to get you started for the remediation.
3. Security Monitoring & Auditing: Besides Manual or Automated scans, security leaders and managers need to stay on top of things by ensuring all the apps are regularly tested for security. Security solutions with features like Store Monitoring come in handy to ease the process and make it more effective.
4. Compliance Monitoring: Ensure that an organization adheres to relevant security standards and regulations. This includes monitoring for compliance with regulations such as HIPAA, SOC2, and PCI-DSS.
It is critical to incorporate testing and monitoring into the development and deployment processes of your mobile app to ensure its long-term security. This will enable you to recognize and address potential security issues as they arise.
07. Train Users
Government app users should be trained on how to use the app securely and how to identify and report potential security threats. Security awareness campaigns should be run on the app interface, which will demonstrate the compliance that a user has to go through while using the app.
Also, its user base is not only limited to citizens but also to government servants. Thus regulating proper user guidance also helps a lot in maintaining the security of any government application
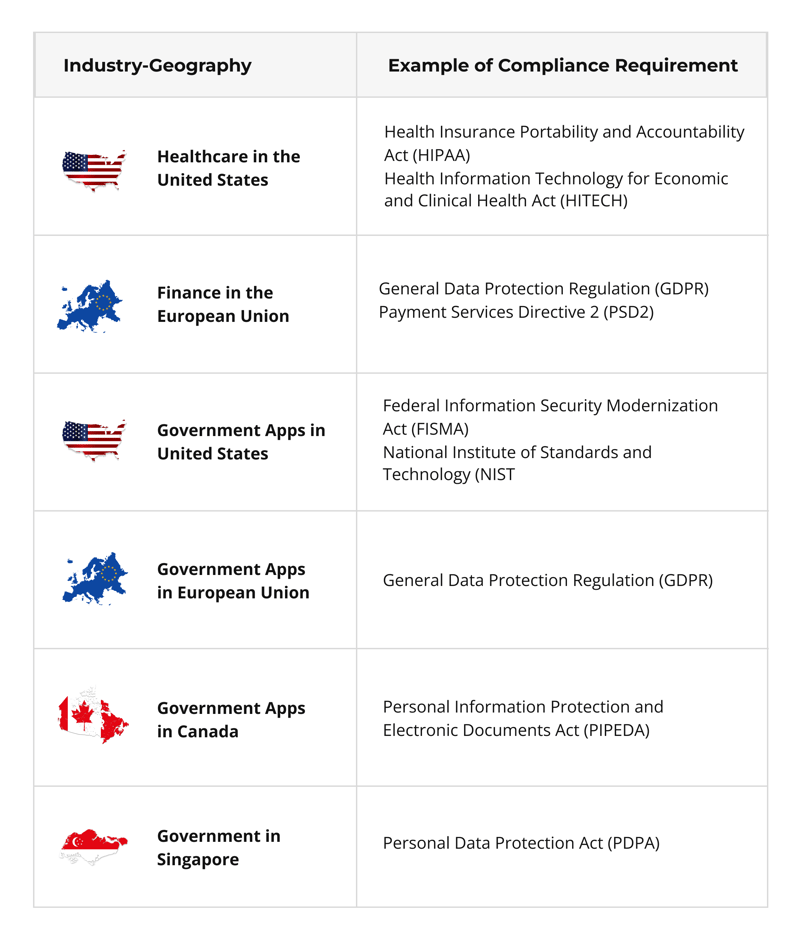
08. Compliance with Regulations
Government apps are subject to various regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). It is important to ensure that the app complies with relevant regulations and that appropriate measures are in place to protect sensitive information.
These compliances can be industry or geography specific, such as:
09. Use Secure Communication Protocols
Secure communication protocols like HTTPS and SSH add an extra layer of security to data sent over the internet. These protocols encrypt data and provide authentication to ensure that only authorized parties receive it.
10. Have an Incident Response Plan
Even after having all the security working properly, it is very common that some things that are not in our hands can get away with it, like the sudden traffic rise in the application during the quarter end and etc. We need to be prepared for that time.
It is important to have an incident response plan in place that outlines the procedures for responding to a security breach. This plan should include procedures for identifying and containing the breach, as well as steps for restoring normal operations.
Video Credits: EyeonTech by TechTarget
A general incident plan looks like this -
Step 1 - Identification of the Incident
Step 2 - Verification of the Incident
Step 3 - Measures for Containment
Step 4 - Steps for Eradication
Step 5- System Recovery
Step 6 - Further Analysis of Root Cause for Learnings for Future
Step 7 - Post-incident Activities (this includes communicating with stakeholders and reporting to regulatory bodies as required)
Step 8 - Closing the Incident
In the event of a mobile app security incident, additional steps in the incident response plan may be required to address issues such as:
a. Obtaining forensic information from mobile devices
b. Detection and revocation of compromised mobile app credentials
c. Communicating with users of mobile apps and advising them on how to protect their devices and data
d. Updating the mobile app to address vulnerabilities and prevent future incidents
Developers should perform proper penetration testing after analyzing the threats and risks and must have different plans and strategies to ensure the safety of the application.
Conclusion
Build a robust, security-first government app with Appknox
Cyberattacks are on the constant hunt for vulnerabilities in government apps in order to expose sensitive data about its military, citizens, finances, and more.
Appknox allows you to integrate DevSecOps into your SDLC to implement security in your apps, from their planning phase to deployment and maintenance. You’ll get a full picture of mobile app security with efficient yet user-friendly automated vulnerability scanning in under 60 minutes with less than 1% false positives.
Appknox offers:
- 1-click SAST, DAST, and API scans
- Manual penetration testing and remediation strategies
- CVSS score and VA reports
Choose cloud or on-premise deployment and secure your apps right now!
