
Guides
A guide to ensuring the security of banking & finance apps
The banking, financial services, and insurance (BFSI) industry is one of the main targets of cyber attackers. In 2023, financial institutions suffered approximately 27.32% of global phishing attacks.
The finance sector is undergoing rapid digital transformation and witnessing huge growth with mobile payments, fintech, etc. According to a survey, 45% of consumers use a mobile application to execute a finance-related task at least once a day.
However, finance and banking mobile apps are highly susceptible to attacks, AI deep fakes, cryptocurrency risks, and third-party breaches. This presents a huge opportunity for hackers to find and exploit mobile app vulnerabilities and conduct cyberattacks.
Common cyber threats in the BFSI sector include phishing, DDoS, ransomware, crypto-mining, botnets, etc., jeopardizing businesses and individuals in terms of reputation and money.
Today, securing your finance and banking apps has become more important than ever, so that you don’t become the next target.
In this guide, you’ll understand a step-by-step process to secure your finance and banking apps from cyber risks.
Table of content
Financial services firms are 300 times as likely as other companies to be targeted by a cyberattack,” according to a report by the Boston Consulting Group. “Dealing with those attacks and their aftermath carries a higher cost for banks and wealth managers than for any other sector.”
You cannot rely on enhancing network or device security to defend your apps in light of the terrible effects of privacy breaches.
Cyber attacks on the web and mobile apps are unfortunately common. As a result, businesses and banks, in particular, will inevitably need to strengthen the security of their apps.
Firewalls and antivirus programs, while helpful, are largely ineffective without these additional safeguards. Fortunately, you may take steps to protect your apps against reverse engineering and tampering without having to set aside a vast sum of money.
Our industry-leading security researchers at Appknox have developed some essential guidelines to help your business reach its cybersecurity goals faster.
Step 1: Identify the need for cybersecurity for your app
The first step in ensuring the security of your banking and finance mobile apps is to understand the existing state of security and identify the improvements needed.
For example, the API architecture of banking apps is a significant entry point for hackers. Public APIs introduce vulnerabilities that cannot be patched or mitigated by using more standard security tools like firewalls or web application firewalls (WAFs).
For instance, APIs and mobile banking apps foster encrypted communications between machines across the network. Attackers can take advantage of machine-to-machine interactions by developing shadow APIs independently. Unfortunately, network firewalls are powerless against shadow APIs, allowing hackers and crooks to masquerade as legitimate users and escape detection.
Similarly, many other areas of concern include code security, data encryption, testing of networks, adherence to standard compliances, etc. Once the need is identified, you can proceed with the security best practices described below.
Appknox Enterprise Offerings for Banking & Financial Apps
-
Continuous integration with IDE and Issue Reporting tools
-
Real DAST connects to devices in the physical device farm
-
Dynamic Induced - API Testing Capabilities
-
Total of 120+ Test Cases
-
Compatible with Android & iOS Applications
-
On-Demand scanning with push of a button from your dashboard
-
Plug into CI/CD tools and enable DevSecOps for your company
Step 2: Factors to consider while developing a secure fintech mobile app
We'll use a few essential definitions throughout this article to help you understand how GDPR will affect your mobile apps.
1) Check the Mobile App Logic for Security
Security is of utmost importance every step of the way.
Store only the data that is important to business
Apple Pay made the idea of tokenization popular by making one-time payment codes with tokens. This was done to reduce the risk of major data breaches.
With this method, you don't have to save the numbers for debit and credit cards. The token will be kept on the servers. The whole system will only deal with the token, and no one will need to know the billing information.
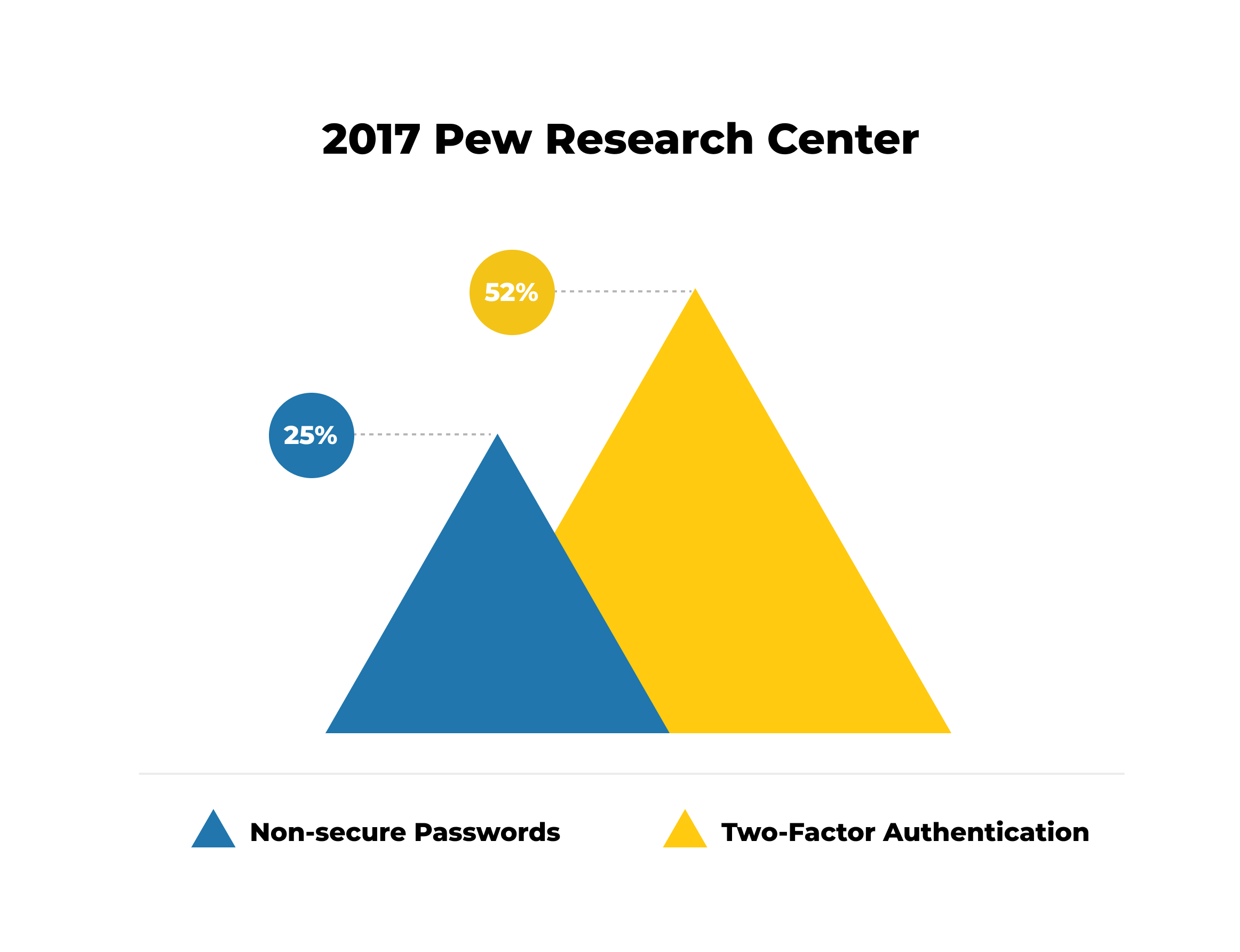
Use of Complex Passwords and Multi-Factor Factor Authentication
Only 52% of American adults use two-factor authentication, and 25% prefer simple, non-secure passwords because they worry they might forget sophisticated ones, according to a 2017 Pew Research Center research.
Keep Track of All the Critical Details
Make sure to log all user activity. For e.g.:
- User Action (Example: Transaction details),
- User ID or account in the platform,
- User IP Address,
- Geolocation,
- Device Data
Ensure your app developers keep logs of everything while creating your mobile banking or fintech app. These logs must be readily available for a future "post-mortem analysis" should any incident need to be reviewed.
Use Multiple-step Approval Procedures for Important Actions
It would be safer to have a multi-step approval process for actions involving significant transactions or changes to important information. Although the customer may occasionally find it annoying, you can never be too careful about security.
When developing a fintech app or a mobile banking app, the following functionalities are also essential to have:
- Don't keep any private data on local computers.
- Always utilize SSL for all communications with your fintech or mobile banking servers.
- Implement voice recognition or biometrics.
- Automatic logout if there has been no action from the user for a set period of time.
- Have SMS messages sent to you for each transaction you make on the app.
2) Ensure the Security of the Code
There is no space for error in mobile banking and fintech apps because they are focused on money and sensitive data. These apps need to be user-friendly and intuitive, but they also need to be safe.
Following specific procedures when developing secure fintech applications or mobile banking applications:
1. Focus on Input Validation
By cleansing or rejecting the input, input validation helps stop hackers from inserting dangerous code into your program. Numerous websites and applications have been compromised simply because input validation was not included.
2. Examine Every Information Sent to an Outside Network.
Make sure that any data your app sends to external networks is essential, and check it to ensure it doesn't contain any sensitive information.
3. Define Access Control
Access controls must be in place to prevent data leakage and unauthorized use while developing a safe financial app.
4. Protect Against SQL Injection
Ask your QA team to use SQL injection attacks to test your app's vulnerability and evaluate its functionality. Make your app impermeable if you want the greatest levels of security.
3) Make Use of a Secure Infrastructure
You should use the best infrastructure for secure fintech app development and mobile banking. Here's how we assist you in doing that:
a. Put Perimeter Defense into Action
This is for your firewalls and proxy servers. Set up your routers correctly to stave off any internal threats.
b. Focus on Operating System and Application Server Maintenance
Use tools like Microsoft's Software Update Service and RedHat's up2date service to keep your operating system in good shape and make sure it is always up to date.
c. Manage Third-Party Components
When using third-party components during mobile banking app development or fintech development, constantly monitor them, keep them in good condition, and regularly update them.
d. Have Redundant Failover Infrastructure
Use the services offered by the AWS cloud to recover from disasters faster and reduce the damage caused by DDoS attacks. Each layer of the technology stack should have a backup plan.
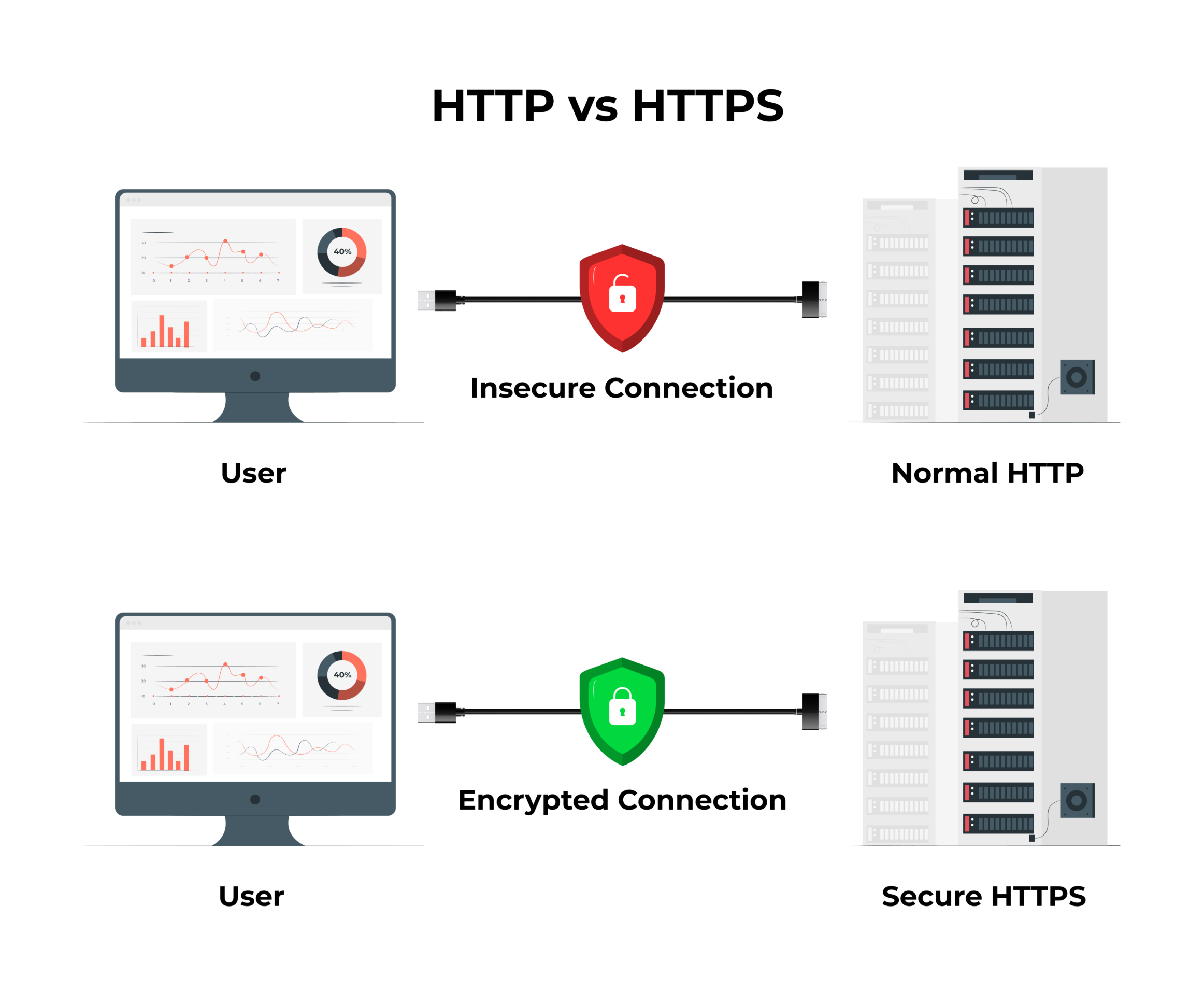
e. Use HTTPS
To keep your users' data safe, use an HTTPS SSL certificate. Use it as the de facto standard for all your mobile app development projects because every request needs to be SSL-secured.
4) Make Sure Everything is Safe
a. Separate Pre-production, Production, and Development Environments
Ensure your developers can only access to the development environment while aiming for secure financial app development. This will guarantee that essential business data is not altered.
b. Implement ISO 27001 Certification
One of the top information security certifications is ISO 27001. As an ISO 27001-certified company, your financial organization can guarantee that your applications adhere to the best standards for security policy, risk assessment, incident management, and other cybersecurity best practices.

5) Test for Every Potential Scenario
Check Network Security
Test the servers, networking equipment, and DNS on your network. Test all components, including the database, storage, and operating system.
Scan Everything from the Client Side
Internal testing or client-side penetration testing: Ensure no breach may happen by checking the program while it is active in the browser. You can use this to execute JavaScript, inject HTML and CSS, clickjack, and test local storage. This will enable you to respond to some crucial inquiries like:
- Is the system vulnerable in any way?
- If so, how can you prevent it? What harm can be done?
- Are everyone's access rights adequately set?
- Are there any systemic weak points?
- Testing for Server Security
6) Implement Data Encryption
In essence, encryption implies providing the original data to the intended recipient while sending useless data to hackers or unauthorized users. It is not sufficient to only use HTTPS or SSL for data transport; all of your databases must also be encrypted.
The Federal Financial Institutions Examination Council recommends that banks and other financial institutions encrypt all of the following data:
- Any personal information a user provides to obtain a particular service or good (like – name, address, income, social security number)
- All a transaction can yield in terms of information (like – payment history, credit card purchases and account numbers)
- Information gathering from rendering a certain financial service (like – a consumer report)
7) Adhere to All Laws and Regulations
You must abide by several financial laws and regulations when developing a secure fintech or mobile banking app. It is best to work with a software development company or engage fintech app developers who are not only knowledgeable about these rules but have also created fintech solutions for other clients in those places because these laws vary between countries and regions.
Follow GDPR Guidelines
From 2018, companies in EU and EEA countries have to follow GDPR rules. This ensures that data is safe and shows how data is processed and what information is used or stored. If you don't follow the GDPR policy, you could get a hefty fine and face other legal problems.
Data Security Standards for the Payment Card Industry (PCI DSS)
PIC DSS aims to protect user data and maintain a secure network by routinely testing and monitoring the system to lower credit card fraud.
Adhere to PSD2
The European Commission approved this proposal, which is in effect as of September 14, 2019. The goal is to assist online payment initiatives like open banking, establish a more secure and cutting-edge payment infrastructure throughout the continent, and facilitate cross-border financial activities.
8) Don't Miss the Next-Gen Technologies
Secure financial app development uses cutting-edge technology like AI, machine learning, or AR/VR to offer a high level of personalization. The software then considers the user's actions and preferences to improve the user's intuitive and gratifying experience.
Big Data
Big data applications in secure fintech app development include fraud detection, risk management, and money management. Data analysis tools are also helpful for FinTech organizations to forecast future trends and weigh potential risks and advantages (for example, when investing a considerable amount of money).
Artificial Intelligence and Machine Learning
Digital assistants (chatbots) and voice-processing technologies are now feasible. These cutting-edge technologies also assist in spotting flaws and irregularities that a human would be unable to find, raising the bar for security.
Step 3: Identify a team to help you deploy a secure banking app
You could jeopardize your business as a result of one cyberattack.
According to data from the National Cybersecurity Alliance, 60% of small and medium-sized businesses shut down six months after an attack. Companies that become targets of hackers and cybercriminals lose the trust of their clients and their repeat business.
This is why selecting a company to handle your firm's cybersecurity needs is an essential investment. Here are some reasons why you need to work with a cybersecurity service right away:
1. Make Sure Your Company Is Safe From Cyber Attacks
Protecting your company from all kinds of cyber-attacks is the primary responsibility of a cybersecurity service provider. Industry-leading cybersecurity partners like Appknox implement security tools like the Appknox SAST and DAST to deter vulnerabilities and hackers.
2. Determine Network Infrastructure Vulnerabilities
Your network may contain security vulnerabilities that hackers could exploit to access your system. One of the first tasks a cybersecurity agency you employ will perform is a thorough network audit to look for vulnerabilities. They will then inform you of their findings and provide a plan of action to seal these security gaps and fortify your network.
3. Offer Training on Cybersecurity Best Practices
Your staff may be your biggest weakness if they lack cybersecurity training. Human mistake is the leading cause and accounts for almost 27% of data breaches, according to the Ponemon Institute's 2018 Cost of a Breach Study. These percentages will drop massively as employees learn about appropriate cybersecurity practices and routines.
4. Improve Your Defenses Against Cyberattacks
Cybersecurity firms will regularly do patch management on every device in the network. The operating systems of each piece of hardware in the network could have security flaws. These security flaws are often "patched" by the people who make these programs. IT teams then download and install these patches on their network devices. Your cybersecurity partner will install these patches and keep them up to date to protect your network from malware that will take advantage of weaknesses.
5. Identify and Remediate Cybersecurity Issues
A cybersecurity service provider will regularly monitor your app's internal processes and check for anything that doesn't seem right. They will also use all the methods they have for scanning for malware and viruses to see if any new types of malware have gotten into the infrastructure. If their methods find something, they will immediately eliminate the malware and get your system back in working order.
6. Support Your Company's Compliance Needs
As consumers become more aware of big data breaches, more and more governments are putting the responsibility of protecting customer data on businesses and corporations. They make laws and penalize those who don't follow them.
One of the best examples is the European Union, which created the General Data Protection Regulation (GDPR) to prevent data breaches and fight cybercrime by preparing companies for these possible problems. A company that doesn't adhere to any of GDPR's regulations could be fined in addition to any damage caused by the infringement.
Ideal cybersecurity partners like Appknox can help your business meet these rules by making sure your security protocols are always up to date. This will help you set your banking or finance app to meet key cybersecurity compliance regulations like PCI DSS, GDPR, OWASP, CCPA, VPPA, and others.
Where to start for apps at different levels of development?
After you have decided to outsource security to your trusted cybersecurity partner, you have to make sure that the transition is smooth and also aligns with the stage of development in which your mobile application currently is (not yet developed, developing, or deployed to production). Based on these factors, these can be your immediate next steps while transitioning security to your cybersecurity vendor:
1. Identify Gaps in Your Existing Infrastructure
The right external security team will keep an eye on threats to your mobile app, both those that occur every day and those that are far away and that you may not know about. They can look at your processes and security protocols, your training, and your software environment. This kind of planning ahead can make you safer online and make it more difficult for hackers to get to you.
2. Focus on Integration and Automation
It is much better and more beneficial for a cybersecurity provider if the partnership is seen as a collaboration by both parties. The strategy will be fully and consistently implemented if it can mesh with your team and the organization. The highest level of automation should be used for routine operations and incident response. Look for solutions that can automate the most time-consuming and ineffective tasks.
3. Upgrade to DevSecOps
DevSecOps lets you address security issues right from the get-go with little to no effort in addressing every security issue that causes potential risks. This could also be your business's potential competitive advantage for faster time to market and uninterrupted business activities.
When you use Appknox during development, you are running DevSecOps optimally. Your App's build is auto-submitted to the dashboard at regular intervals, while continuous integration allows your app to be tested against updated and evolving threats. Test results are then submitted to the developers to make necessary changes or enhancements.
4. Focus on Cybersecurity Training
In addition to your security vendor, your in-house teams also need to stay vigilant and make sure their actions don’t open new gateways for threat actors. So, while transitioning your affairs to a new cybersecurity vendor, it becomes essential to train your own employees on cybersecurity best practices as well.
5. Switch to Automated Mobile Application Security Testing
Enterprises should conduct regular security testing on the application to prevent vulnerabilities present in the application and ensure best coding practices that are secure as well.
6. Get Compliance Ready from the Start
One of the biggest issues faced by corporate boards nowadays is regulatory compliance standards. The typical enterprise has been turned inside out over the past two years. All companies require an always-connected defensive posture and clarity on what business risks distant users elevate to remain secure as the new normal of hybrid work begins to take hold.
Conclusion:
Hack-proof your finance and banking apps with Appknox
As cyberattacks on the finance and banking industry never seem to cease, the only option you have is to implement advanced security strategies and technologies to prevent the likelihood of security incidents.
With Appknox, you can leverage advanced app security testing solutions - automated vulnerability assessments (VA) and manual penetration testing. We’ll also help you integrate DevSecOps into your SDLC to protect your apps from the ground up.
Take the security-first approach for your app with:
- 1-click SAST, DAST, and API scans to discover vulnerabilities in under 60 minutes
- Detailed VA report with CVSS scores
- Suggestions to remediate vulnerabilities
- Option to choose a security solution between on-premises or cloud deployment
