
BLOG

BLOG
In 2022, Twitter suffered a massive data breach, which exposed the personal data of 5.4 million caused by broken authentication. Threat actors exploited Twitter's API vulnerability to gain unauthorized access to users' sensitive personal data. The incident resulted in reputational loss and hefty fines from the regulatory body for failing to protect users' data.
This shows that no organization, regardless of size, is immune to data breaches.
A SALT report on the State of API Security Risks, 2023, confirms the trend. According to the survey, 94% of respondents verified increased API security-related issues in their organizations.
Recognizing the urgency of dealing with security breaches, the OWASP (Open Web Application Security Project) published guidelines to avoid the recurrence of such incidents.
This guide provides detailed information on OWASP's Top 10 security risks and suggests ways to comply with them.

The Open Web Application Security Project, popularly known as the OWASP, consists of the top 10 critical security risks compiled by the leading cybersecurity experts worldwide.
The OWASP sets application security standards for developers, and the list is updated every 2-3 years as new security challenges emerge with the stated mission to make the web a safer place for everyone.
OWASP’s resources are globally recognized, and developers use their open-source tools, training material, and other insightful resources to develop secure applications and mitigate security threats.
However, the vast number of potential vulnerabilities can overwhelm security professionals. OWASP made the task easier by prioritizing the most common and serious security vulnerabilities.
New threats constantly emerge that require a change in security posture. Here’s a list of OWASP Top 10 Vulnerabilities 2023 that will help you understand the risks and learn the best mitigation strategies.
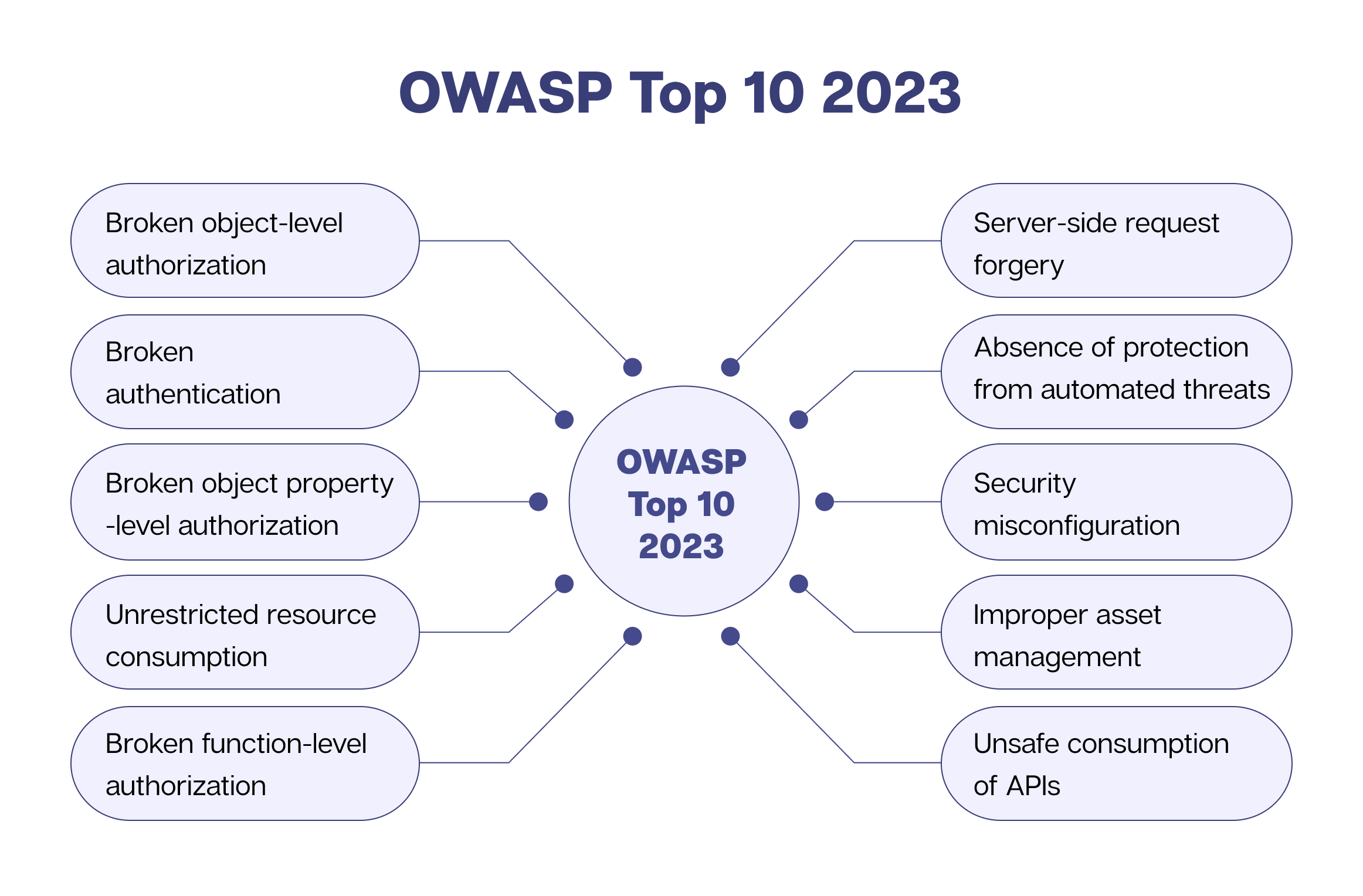
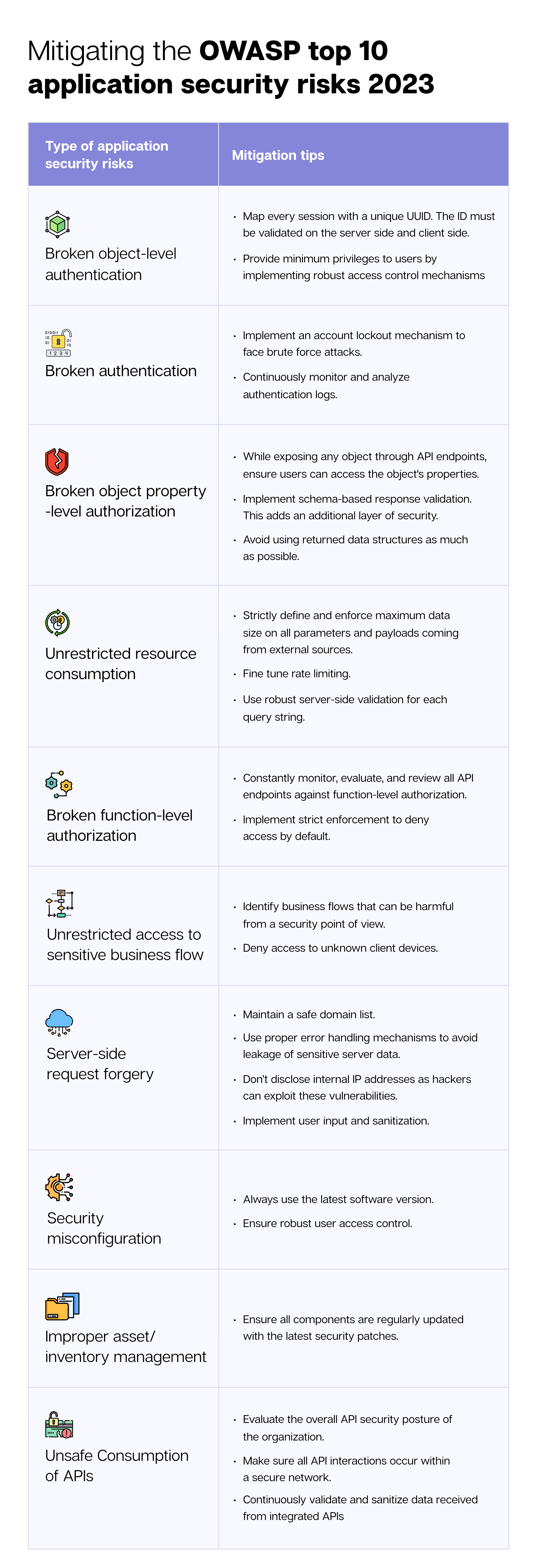
Broken object-level authorization refers to unauthorized access to restricted data sources in web applications. According to OWASP, this is among the most common cybersecurity risks faced by 94% of web applications.
It occurs because application server components fail to track and monitor the client’s state, as they rely mainly on Object ID parameters to decide to request permission. Each API endpoint receiving an Object ID and performing any action is potentially vulnerable to this security risk.
The absence of a proper user access control mechanism in authentication, authorization, validation, and session management can also result in application security breaches.
Broken authentication is critical to application security, as it validates users' identities before allowing them to access a protected resource. This is like a security gateway for any application. So, it is essential to monitor a user's identity, authentication, password security management, and session management.
With the introduction of two-factor authentication (2FA) and other stricter authentication measures, broken authentication issues have come down, but they are still significant.
Broken object property-level authorization occurs when an application programming interface (API) provides authorization to data objects based on the user's role but fails to ascertain whether the user is allowed to access those specific data entities.
It focuses on the security of a system's access control configuration and its power to limit liberties at the object property level.
The immediate impact of these exposures is that attackers have unauthorized access to sensitive data. It is a common issue because the server component depends more on external parameters.
Unrestricted resource consumption is a continually overlooked API vulnerability. API requests consume CPU, memory, network, and storage resources. This attack can be carried out by transmitting multiple requests to the target system.
This OWASP vulnerability ensues when an application fails to specify the consumption of resources, such as CPU cycles, memory, or network bandwidth.
Unrestricted resource consumption can make the targeted system unstable or unavailable, which can have severe consequences for the business or organization that depends on it. It can also result in denial-of-service (DoS) attacks and other malicious activities.
The broken function-level authorization vulnerabilities encourage unauthorized users to access certain functions, features, and privileges they should not have access to.
Once the attackers access unauthorized resources, they exploit broken function-level authorization vulnerabilities to create/delete accounts, take over another user's account, and escalate privileges to gain administrative access.
This OWASP Top 10 API security vulnerability mainly occurs due to inadequate authorization checks, input validation, and weak access controls.
SSRF or Server-Side Request Forgery events occur due to a distant resource's lack of URL validation. Malicious actors often send requests to servers from unknown locations, bypassing VPN or firewall protection.
Hackers can successfully do this by manipulating URLs. They can achieve this goal by replacing the existing URL with a new one. They can also tamper the URL through the URL path traversal technique.
As automation technologies such as bots become more challenging to detect and safeguard against, the threat of malicious cyber attacks, such as brute-force attacks, distributed denial-of-service (DDoS) attacks, and credential stuffing attacks, proliferates.
Although the APIs may not have inherent bugs or flaws, the underlying business flow is susceptible to excessive activity. Hackers quickly comprehend the API models and business flows and eventually exploit them to their advantage using automated tools.
Such automated attacks can have serious consequences, including security issues without adequate protection, system downtime, data breaches, and financial losses.
Not implementing security configuration settings properly leaves applications vulnerable to cyber threats.
Misconfigurations often arise from various sources, including
● Weak passwords,
● Inappropriately configured databases and cloud applications,
● Misconfigured firewalls or network settings, and
● Outdated firmware, leading to data theft, denial-of-service attacks, and malware attacks.
Using improper inventory/asset management, such as outdated application components, can compromise an entire application's security.
That is why developers should know the versions of system components and regularly perform security audits to detect potential vulnerabilities and prevent them.
APIs are a treasure trove for hackers because they are a doorway to valuable information.
While APIs deliver tremendous benefits, such as quicker development time and improved agility, they pose new security risks if not adequately addressed. In a typical attack scenario, a threat actor manipulates a third-party API.
The attacker determines a weak third-party API and exploits it. The not-so-safe consumption of APIs can cause malicious code execution, data leakage, and escalation attacks.
Following these actionable tips can help in mitigating the OWASP security vulnerabilities:

Most teams are familiar with the OWASP Top 10 as a list. Far fewer treat it as an operational control framework.
The difference lies in how consistently OWASP risks are detected, measured, and governed across applications and releases.
Detecting OWASP Top 10 vulnerabilities starts with consistent, repeatable scanning, not one-time assessments.
Effective detection combines:
Static analysis to uncover insecure code patterns
Dynamic testing to validate runtime exploitability
API testing to catch authorization and data exposure flaws
Together, these approaches ensure coverage across both design-time weaknesses and runtime risks.
Detection must run continuously across builds, environments, and releases to prevent OWASP risks from reappearing silently over time.
OWASP Top 10 is often referenced in compliance conversations, even when it’s not a formal regulatory requirement.
Auditors and risk teams expect organizations to demonstrate:
That OWASP risks are actively tested
That findings are tracked and remediated
That testing aligns with internal security standards
Ensuring tests meet OWASP compliance means detection is:
Documented
Repeatable
Verifiable across time and applications
This is how OWASP moves from guidance to defensible security evidence.
Not all OWASP Top 10 findings carry the same business risk.
Assigning risk scores, typically using CVSS or internal scoring models, helps teams:
Prioritize remediation
Allocate engineering effort effectively
Communicate the impact clearly to leadership
Risk scoring transforms OWASP findings from technical alerts into decision-ready risk indicators.
Without scoring, teams fix what’s loud. With scoring, they fix what matters.
As application portfolios grow, spreadsheets and static reports stop working.
Dashboards enable teams to:
Monitor OWASP Top 10 exposure across applications
Track remediation progress over time
Identify recurring or systemic weaknesses
For leadership, dashboards provide confidence that OWASP risks are under control, not just detected.
OWASP Top 10 detection is not a checkbox; it’s a maturity curve.
Organizations mature when they can:
Confirm OWASP coverage across all critical apps
Demonstrate declining risk trends
Prevent repeat findings across releases
At this stage, OWASP Top 10 becomes a baseline security expectation, not an ongoing firefight.
📌Key takeaway: OWASP Top 10 reduces risk only when detection, scoring, and compliance are enforced continuously.
Below are some of the recommended best practices to stay OWASP compliant:
Familiarizing yourself with the risks is the most effective way to stay OWASP compliant. OWASP Top 10 Application Security Risks 2023 does a fantastic job of creating a valuable repository of the latest security risks and assisting developers in staying informed of various types of application security risks and best practices for application security.
Most web security risks start with ignoring basic security aspects. Most developers view adhering to security standards as an unnecessary burden, failing to realize the long-term implications of ignoring security protocols while coding.
Ensure your tech team implements the best DevSec practices.
The cybersecurity risk landscape is not static - new risks are continuously evolving. Regular security audits and vulnerability scanning should be part of your organizational culture.
To do this, a good-quality vulnerability scanner must be run to identify and fix common OWASP vulnerabilities.
Though the OWASP list offers a good starting point for security teams, manually identifying the gap in the application’s security environment is challenging and time-consuming.
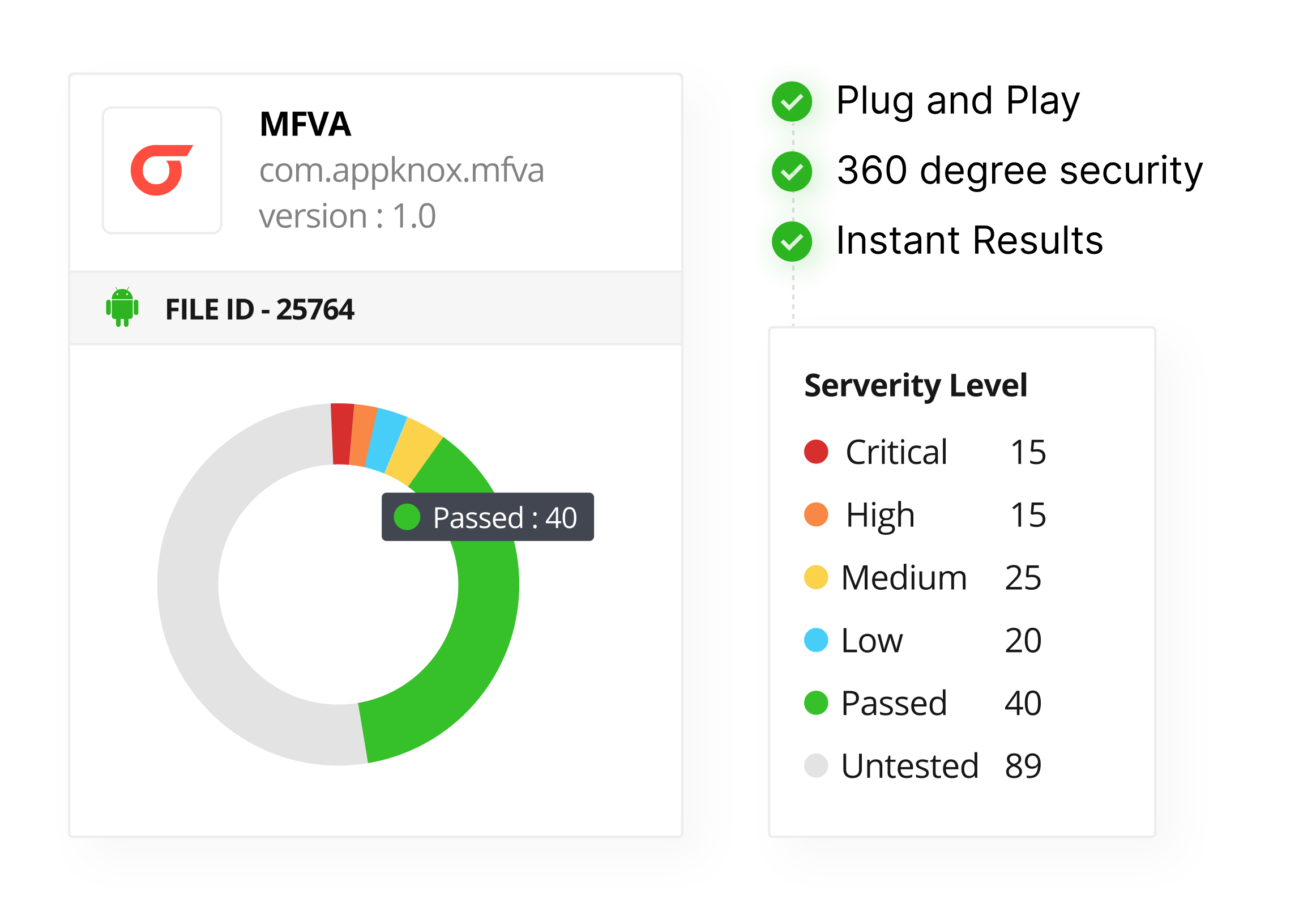
Appknox is a binary-based automated vulnerability assessment tool that quickly identifies and tracks security gaps. After scanning your application, Appknox generates a detailed CVSS report containing potential vulnerabilities mentioned in the OWASP Top 10 list and actionable remediation notes.
.png?width=2324&height=1392&name=image%2002%20(1).png)
This enables your security teams to understand the risks and fix them promptly. Thus, at Appknox, we ensure your app meets the highest security standards.
Though OWASP guidelines are optional, unlike HIPAA, GDPR, and other data standards, the document serves as a benchmark for security professionals worldwide. Non-compliance with these guidelines will lead to data breaches, financial losses, hefty fines, and loss of reputation.
Assessing OWASP application compliance is a complex task requiring an in-depth assessment of vulnerabilities. Using penetration testing and vulnerability assessment tools provides a 360-degree view of security risks.
These tools can identify risks that may be overlooked during a manual security assessment. Some application security testing tools provide a score after a detailed assessment of security scenarios.
OWASP compliance demands a multipronged approach to evaluate the overall security posture and implement security controls and secure coding practices.
Appknox can identify potential weaknesses in application security and proactively detect them before they escalate into significant security issues. This helps to prevent potential security breaches and data leaks.
By combining static, dynamic, and API security testing that maps findings directly to OWASP Top 10 categories and runs continuously across releases, you can detect OWASP Top 10 vulnerabilities.
Leaders can monitor OWASP Top 10 risks through centralized dashboards that track OWASP findings, remediation progress, and trends over time.
Risk scoring helps teams prioritize remediation based on real business impact instead of fixing issues in arbitrary order.
You can review compliance status against OWASP Top 10 by maintaining verifiable scan records, remediation tracking, and risk scoring aligned with OWASP categories and internal security standards.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
