
BLOG

BLOG
Since its arrival on the cyber security landscape, SQL injection has continued to be one of the topmost cyber security concerns. As a hacking technique, it is known for its devastating capabilities and the havoc it can cause for institutions of any size and type. Moreover, the frequency of such attacks grew exponentially by around 44% in two years (from 2017 to 2019).
Not to mention, this technique has been used in activities ranging from personal data theft during the US presidential elections to high-profile security breaches at Sony, Microsoft, Yahoo, and even CIA.
Here, we have compiled a list of tools that aid in the detection of SQL injection attacks and a few essential steps to prevent such attacks.
But before proceeding, let's examine how injection attacks can impact your business and whether you are vulnerable to them.
SQL, or Structured Query Language, is the preliminary language for manipulating the most widely used relational databases, such as Oracle, Microsoft SQL Server, and MySQL. These databases are the basic building blocks of modern-day web apps and content management systems.
Threat actors who wish to compromise your security systems through SQL injection attacks are after the sensitive data stored in your databases. These database servers control and curate the content and behavior of applications and websites.
So, if your servers hold sensitive data, which is usually the case, you are vulnerable to SQL injection attacks.
If hackers, by any means, gain access to your critical databases, the results could be catastrophic. In a severe event like an SQL injection login bypass attack, the threat actors could gain unprecedented control over the entire system and access and modify critical business or customer data.
An SQL injection attack could result from disrupting website or application content or breaching sensitive user information. If you understand the role databases play in the back-end, you surely would realize how devastating it could be if a hacker executes a simple SQL injection command like DROP TABLE!
After understanding the potential consequences of SQL injection attacks, thinking of ways to prevent them becomes imperative. The primary step in avoiding an SQL injection attack is to determine the elements of your system that are potentially vulnerable to it.
The best way to test your defense is to check it with your weapons. However, given the complexity of SQL, the task won't be as easy as it sounds. It is generally a complicated task to create a code snippet and inject it into a query to compromise a relational database.
On the other hand, deploying some specialized tools could make this seemingly difficult task easy. These automated SQL injection attack tools could replicate real attack scenarios and help you thoroughly test your system.
Let's take a look at some of the most commonly used tools to detect and prevent SQL injection:
One of the most frequently used tools for identifying and exploiting SQL injection flaws, Sqlmap, is an open-source pen-testing tool that provides extensive security to database servers. Apart from several other functionalities, the most exciting feature of Sqlmap is its powerful detection engine, which quickly detects injection flaws in the system. Experts also recognize a GUI version of SQLmap, known as TyrantSQL, as a promising automated tool.
Developed by Iranian cyber experts, Havi instantly determines the database details of the target system by quickly getting through its security layers. Havij later builds complex queries using the acquired database knowledge to dive deeper into the detailed database characteristics. Without much knowledge of SQL, security professionals can extract tables, fields, and even bigger chunks of data from the target database using Havij.
The error-fixing feature in the tool helps you correct some of the identified vulnerabilities as well. Available in both open-source and licensed versions, Havij is famously known for its functionality across the data security market.
Designed especially for blind SQLi attacks, BSQL hacker is a well-to-do injection tool. With GUI and console support, it supports most of the injection points, including HTTP, cookies, and query strings. It also supports Oracle, MySQL, and MSSQL.
This tool works for web applications based on SQL Server. After discovering injection flaws, it efficiently automates the process of exploitation and extracts all the necessary information from the database. By allowing remote access to the database servers, SQLninja allows the overall security assessment of the web application.
Other prominent SQL injection tools include JSQL, Safe3 SQL Injector, and SQLSus.
Related Topic- Biggest Threat to Application Security: SQL Injection Attacks
One crucial aspect worth noticing here is that these tools not only enable security experts to assess their systems but also supplement threat actors with an arsenal of SQL injection techniques. For these reasons, you should test your applications with these mentioned tools beforehand and fix the suggested vulnerabilities before someone else can exploit them.
It doesn't matter how frequent SQL injection attacks are or how much they can harm organizations and their customers. There certainly are ways to help prevent them. The solutions might not be foolproof, but they could put sufficient barriers for hackers if they attempt an SQL injection attack.
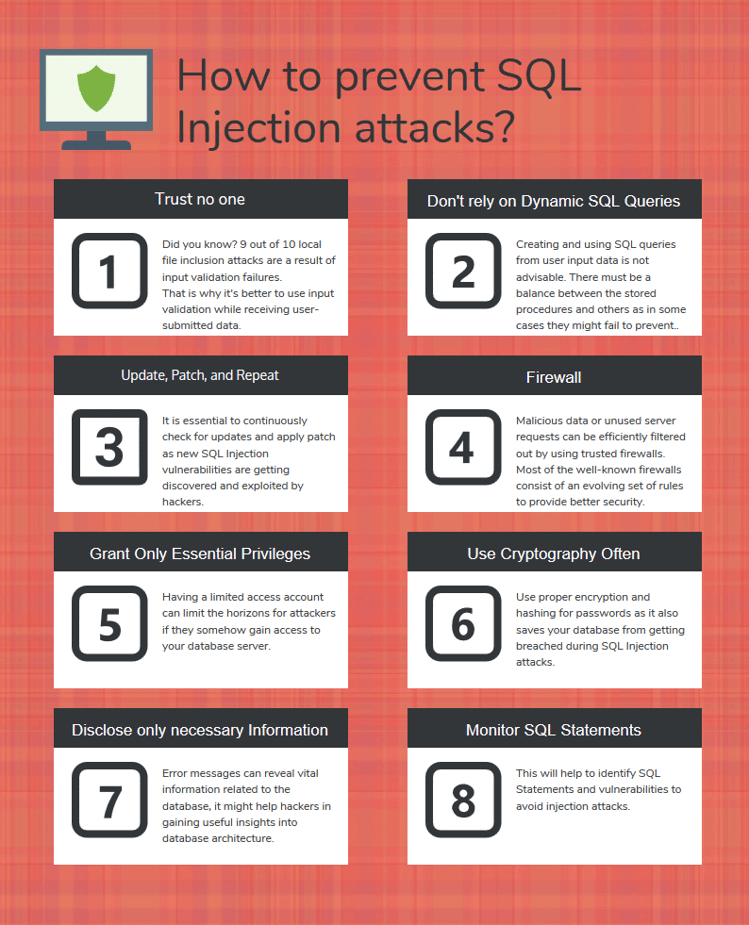
Here are some guidelines on drastically reducing the risk and impact of SQL injection attacks.
According to a security report, 9 of 10 local file inclusion attacks result from input validation failures. That is why it's better to use input validation while receiving user-submitted data. You can't trust what the user intends to do, and user input validation via appropriate functions would filter out any unnecessary characters like 'in SQL queries from the user input data.
Data should also be filtered by context. For example, you should only allow those characters and numbers that are valid in email addresses and only those digits that are allowed in phone numbers.
Creating and using SQL queries from user input data is not advisable. Utilizing stored or parameterized queries and prepared statements is better, as even the best data-cleaning procedures could have flaws. However, there must be a balance between the stored procedures and others, as in many cases, even they might fail to prevent SQL injection attacks.
Hackers regularly discover and exploit new SQL injection vulnerabilities. That is why it becomes essential to continuously check for updates and apply patches as soon as possible. You can also rely on a patch management system to handle your worries.
Trusted firewalls can efficiently filter out malicious data or unusual server requests. Most well-known firewalls have an evolving set of rules to provide the best possible security protection. They can provide some underlying security even against newly discovered threats before a patch is available.
One commonly used firewall is ModSecurity, which is available for various web servers, including Apache and Nginx. Its ever-evolving data security rules are best known for filtering dangerous server requests. Its ability to nullify SQL injection attacks has made it a favorite among similar choices.
It's not necessary to always connect to your database using accounts with admin-level privileges. It should be done only under compelling circumstances. Having a limited access account can limit attackers' horizons if they somehow gain access to your database servers. Suppose an attacker gains access to the code behind your login page. If he gets only limited access to the database, the breach wouldn't be as damaging as it could be.
In a shrewd world, keeping your secrets as classified as possible is better. Proper encryption and hashing for passwords are always considered safe practices and prevent your databases from being breached during SQL injection attacks.
Even error messages can reveal a great deal of vital information related to the database. This might help hackers gain useful insights into database architecture. That is why care must be taken before disclosing any added information anywhere over your platform. Using verbose error messages that reveal nothing about the concerned database might help the cause.
SQL statements from applications connected to the same databases must be regularly assessed to avoid injection attacks. This helps filter unwanted statements and other critical vulnerabilities. Techniques like behavioral analysis and monitoring tools that rely on machine learning can prove useful.
Related topic: A Detailed Overview of SQL Injection Attacks
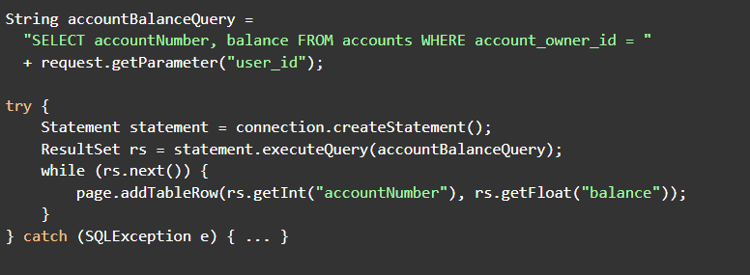
Imagine a developer needs to show the account numbers and balances for the current user’s ID as provided in a URL. They might write (in Java):
Under normal operation, the user with ID 984 might be logged in and visit the URL:
https://samplebankingwebsite/show_balances?user_id=984
This means that the account balance query would end up being:
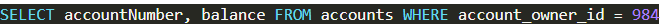
This is passed to the database, and the accounts and balances for user 984 are returned, and rows are added to the page to show them.
The attacker could change the parameter “user_id” to be interpreted as:
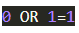
This results in the account balance query being:
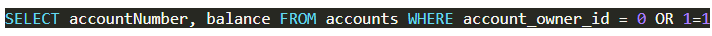
When this query is passed to the database, it will return all the account numbers and balances it has stored, and rows are added to the page to show them. The attacker now knows every user’s account numbers and balances.
You could easily repair this vulnerability by using a prepared statement to create a parameterized query as below:
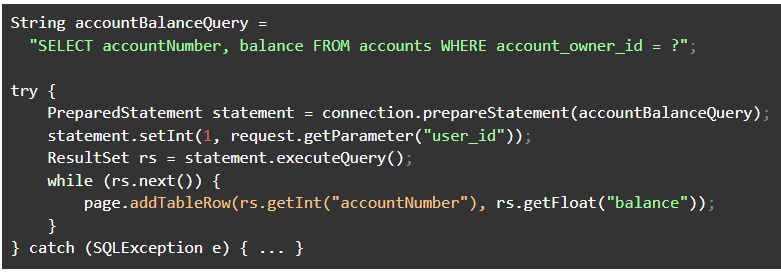
If an attacker attempts to supply a value other than a simple integer, statement.setInt() will throw an SQLException error rather than permitting the query to complete.
Imagine a developer implements a login form and writes (in Java):
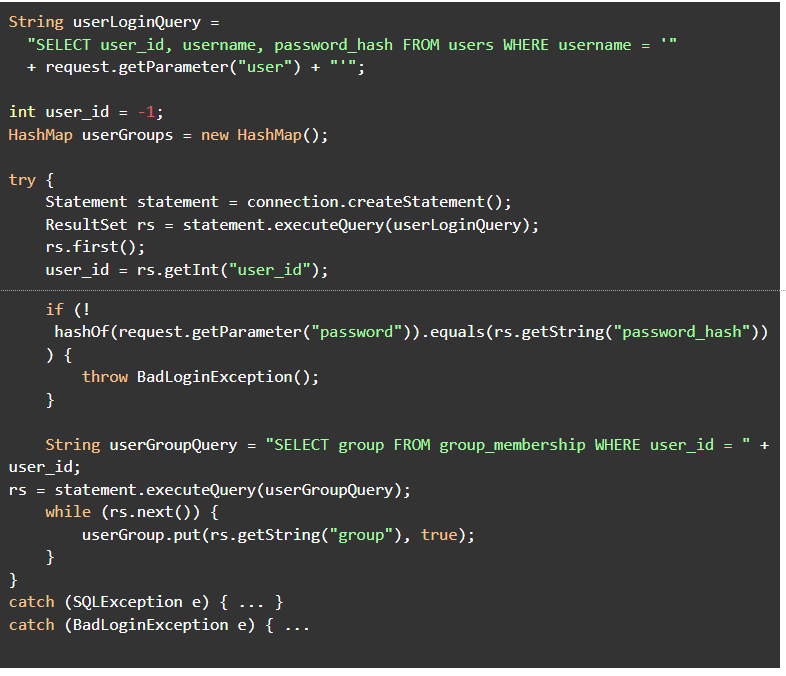
Normally, a user would provide a username (say “Alice”) and password, and the first query executed would be:

The database returns Alice's user ID and password hash, which is then compared to Alice's password. The database then gets the list of groups to which Alice belongs.
However, if an attacker has Alice's password (maybe the attacker is Alice!), they could make Alice an admin. They’d log in using the following as a username (newlines added for ease of reading):
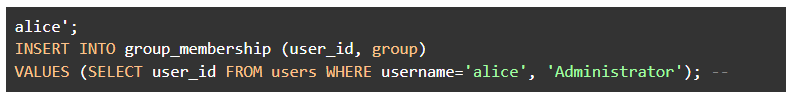
This means the query passed to the database would be:
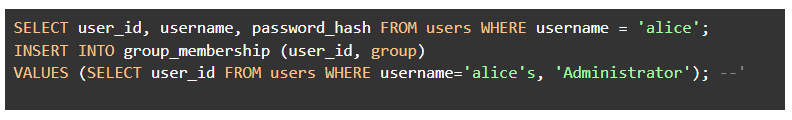
Note that the single-quote character in the input results in the remainder of the input being interpreted as part of the SQL statement rather than part of the value. Alice will now belong to the group “Administrator.” Note that the attacker can change Alice's group without completing the login process in this scenario; that means an attacker who hasn’t guessed Alice's password could perhaps delete accounts, reset passwords, and the like.
The developer could easily repair this vulnerability by using a prepared statement to create a parameterized query as below:
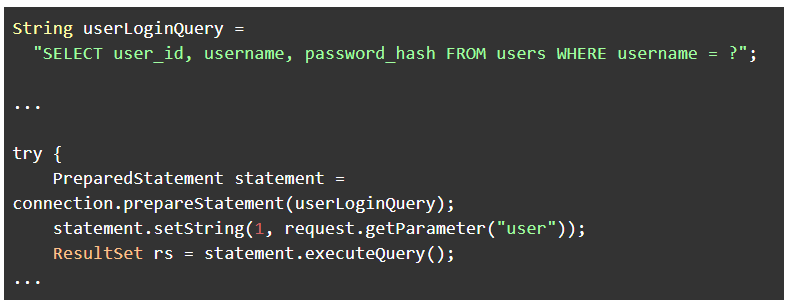
This query will return no results when the 'user' parameter contains an SQL Injection attack since the PrepareStatement sanitizes the parameter's value.
Despite the grueling outcomes, organizations still don't realize the gravity of SQL injection attacks. It's high time that business owners understand this risk and move forward with prevention techniques. The message is simple and clear—if your business relies on an SQL database system, you have to take every possible step to stay safe from the threat of SQL injection. Abiding by a few simple steps will not only safeguard your customers but also save your business.
Appknox SAST can accurately identify SQL injection vulnerabilities and other flaws in your application and its third-party library components and tell your developers exactly where and how to repair them. This is all done without ever looking at the source code further. The issues can then be pushed to Jira.
Appknox plugins with Popular CI/CD tools to test for security issues on each build like Azure, Github, Gitlab, Jenkins, and bitbucket.

Our 360 degree-application security platform helps you manage your application security program, track progress, and educate your developers on avoiding and repairing SQL injection and other security flaws.
