BLOG

BLOG
31% of executives cite improper risk identification as their organizations’ top cybersecurity challenge. Reacting only to attacks leads to an average 118-day breach detection time, which can significantly impact business.
Staying informed about cybersecurity risks is crucial. OWASP offers a list of common threats for testers, but some find them insufficient due to its crowdsourced nature. Mobile Application Security Verification Standard (MASVS) and Mobile Application Security Testing Guide (MASTG) offer predefined methodologies to test against threats. MASTG outlines steps to fulfill MASVS security requirements, aiding in proactive defense strategies.
The OWASP Top 10 ranks the most critical mobile app security risks based on expert consensus. It is a crucial resource for developers, testers, and security professionals to proactively address any security flaws in their mobile applications.
Founded in 2001, OWASP aims to enhance software security globally. Initially focusing on web applications, it evolved into the Mobile Security Project to formalize mobile app security standards.
The OWASP Mobile Top 10 list is regularly updated to keep up with the ever-changing security landscape. Each risk mentioned in the list represents a potential weakness that malicious actors can exploit to compromise the confidentiality, integrity, and availability of mobile app data, functionality, and privacy.
However, the cybersecurity landscape constantly changes, and newer vulnerabilities are often discovered, causing the threat landscape to evolve. So, this often alters the frequency of the list’s publication. This list is collated by collecting feedback from cybersecurity experts on the most critical vulnerabilities in the market.
.png?width=2324&height=3032&name=How%20to%20successfully%20conduct%20penetration%20testing_%20(1).png)
Understanding the major vulnerabilities is important for a cybersecurity leader to manage capacity and resources effectively. By prioritizing security efforts, organizations can fortify their mobile applications against emerging threats and stay ahead in the rapidly developing cyber landscape.
We are adding an OWASP Mobile Top 10 checklist to help you understand emerging threats and their mitigation, as well as the steps to prevent these vulnerabilities while understanding your attack surface.
Exploiting this vulnerability can lead to data theft, invasion of privacy for the company and your customers, economic fraud leading to significant loss, and damage to the company's reputation.
|
Exploitability |
Easy |
|
Detectability |
Easy |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
Hardcoded passwords, also called embedded credentials, are plain-text passwords and other confidential information in the source code.
2. Insecure storage of credentialsStoring user credentials locally on the device exposes sensitive information.
3. Weak password policiesSimple passwords and lack of complexity make it easier for hackers to guess or crack passwords through brute force attacks.
4. Inadequate encryptionTransmitting credentials without proper encryption also exposes sensitive information to be exploited during data transmission.
5. Insecure authenticationIf multi-factor authentication is not in place, attackers can easily gain access using compromised passwords.
6. No session managementIf sessions don’t expire after inactivity, it might expose users to session hijacking and other related attacks.
You can fortify your app by:
Encryption is one of the basic principles of mobile security. Ensure that sensitive data, including credentials, is transmitted and stored using robust encryption methods.
2. Enforcing strong password policiesStrong passwords require users to create and update complex and unique passwords regularly.
3. Enforcing secure authentication methodsImplementing multi-factor and two-factor authentication (2FA) will add an extra layer of security.
4. Improving session managementImplement secure session management practices - session expiry after a brief period of inactivity.
This vulnerability focuses on the activities involved in building and distributing the application. Hackers can exploit vulnerabilities in third-party libraries to access the server backend, manipulate sensitive data, and carry out denial-of-service attacks.
|
Exploitability |
Average |
|
Detectability |
Difficult |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
1. Vulnerabilities
Flaws in third-party applications' source code, such as a lack of data validation or buffer overflow attacks, can create exploitable vulnerabilities.
2. Insecure integration
If the integration between the third-party app and your IT resources is not secure, it might expose you to attackers. Plugins, connectors, and extensions can contain innate security vulnerabilities.
3. Insecure data management
If the app you integrate doesn’t encrypt the data you upload, it makes it easy for attackers to access your private data.
4. Misconfigured access controls
Weak access controls within third-party software that connects to your business can give attackers access to your entire IT infrastructure.
5. Compromised build environment
Attackers can infiltrate the build environment used for compiling and packing your app.
6. Trojanized app release
The compromised build environment can lead to the release of a trojanized version of your app. Your customers may download this version assuming it to be a legitimate version.
7. Malicious code injection
Once inside your build environment, attackers can inject malicious code into the app source code and execute unauthorized actions.
1. Code signing and integrity checks
Implement regular integrity checks and code signing to detect unauthorized modifications to the source code.
2. Dependency scanning
Regularly conduct SBOM security analysis and update dependencies used in the application. SBOM is a collection of all components in a software’s codebase.
With Appknox’s SBOM solution, you can track and identify vulnerabilities in your entire software with just one upload.
Regularly update and patch all build infrastructure components to prevent and minimize vulnerabilities.
User authentication and authorization problems can lead to the execution of over-privileged functionality actions, which in turn can result in the theft of sensitive information.
|
Exploitability |
Easy |
|
Detectability |
Average |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
Insecure value comparisons in PHP & JavaScript can lead to vulnerabilities. Loose comparisons like == can allow bypassing authentication.
Use strict comparisons with the === operator or dedicated comparison functions to mitigate.
2. Path-based authenticationAuth bypass risks arise when access control relies on path comparison. Attackers exploit parsing inconsistencies to traverse directories.
Input sanitization is crucial to prevent such vulnerabilities.
3. Implicit trust in authentication sourcesIn complex architectures, auth responsibilities may shift, leaving the back end vulnerable to API path traversal exploits and exposing sensitive data.
4. Missing function-level accessIdeally, each query should only return data that the user can access.
But this is easy to forget, and any error at any stage allows users unauthorized access to sensitive information. This is common when adding a GraphQL layer to an existing REST API.
5. Token mismanagementIf attackers obtain a valid access token, such as a session cookie, they could hijack sessions, especially with intricate single sign-on setups. Misconfigurations might enable intercepting tokens via redirects or reading them from server logs.
Generate a unique token and validate it for each user session.
2. Role-based access control (RBAC)Define and enforce user roles and permissions.
3. Add multi-factor authenticationThis will require users to provide multiple forms of identification, such as passwords, OTPs, and/or biometric data.
4. Avoid insecure design patternsInsecure design patterns can be avoided by diligently planning threat modeling, proactive vulnerability management, tried-and-true architectural patterns, and SDLC.
Applications that do not perform sufficient data validation, risk SQL injection, common injection, or cross-site scripting attacks are vulnerable to this threat.
|
Exploitability |
Difficult |
|
Detectability |
Easy |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
Insufficient input/output validation arises when it needs to validate and sanitize user inputs and outputs effectively. In essence, if the app doesn't rigorously inspect and filter the data it receives from users and returns to them, it becomes susceptible to various attacks.
Enforce strict input validation by clearly defining and adhering to appropriate data formats. Employ input validation libraries and frameworks to detect and filter out malicious inputs automatically.
2. Parameterized queriesThese are SQL queries in which placeholders are used for input values rather than directly inserting the values into the query string. The placeholders are then replaced with the actual values using query execution, helping prevent SQL injection.
3. Output encodingEncode or escape potentially dangerous characters in the application's output before sending it to the user’s browser. This prevents attackers from injecting malicious scripts or content into web pages.
4. Data whitelistingIt involves specifying acceptable data inputs, allowing only approved values. Data whitelisting filters user inputs, permitting only predefined values and enhancing security.
This vulnerability commonly occurs in mobile apps interacting with servers and external services. Without robust encryption and security measures like TLS/ SSL, attackers can exploit these weaknesses through eavesdropping and man-in-the-middle attacks, compromising data integrity and confidentiality.
|
Exploitability |
Easy |
|
Detectability |
Average |
|
Technical Impact |
Severe |
|
Business Impact |
Moderate |
In this phase, attackers will intercept traffic before it reaches its destination. They can attack using IP spoofing, ARP spoofing, or DNS spoofing.
2. DecryptionOnce a data stream has been intercepted, decryption begins. The goal is to decrypt without raising concerns. The attacker can use HTTPS spoofing, SSL Beast, SSL Hijacking, and SSL Stripping.
HTTPS encrypts data during transit, and TLS ensures end-to-end encryption, preventing eavesdropping and data tampering.
2. Certificate pinningThis will help you validate the authenticity of your server’s SSL certificate.
3. API security measuresImplement robust authentication mechanisms for APIs, such as API keys, OAuth tokens, and other methods.
Inadequate privacy controls mean there aren’t enough security measures, such as strong encryption, access controls, session management, consent methods, etc., to keep user and other confidential information safe.
|
Exploitability |
Average |
|
Detectability |
Easy |
|
Technical Impact |
Low |
|
Business Impact |
Severe |
Hackers can bypass authorization mechanisms, gain unauthorized access to resources, or manipulate object references by tampering with parameters in URLs or API requests.
2. Insecure cryptography implementationWeak or improperly implemented cryptographic functions may render encryption ineffective, allowing hackers to decrypt sensitive data.
This might occur due to outdated encryption algorithms, improper key management, or insufficient entropy in generating cryptographic keys.
3. Information leakage through comments and metadataSource code comments, debug information, or version control metadata may expose sensitive information about the app’s functionality or data structures.
4. Cross-site request forgery (CSRF)The lack of CSRF protection in the source code enables attackers to trick authenticated users into performing unauthorized actions that compromise privacy controls.
5. Insecure data storageStoring sensitive information such as passwords and personally identifiable information in plaintext or insecurely encrypted formats can result in data leakage.
6. Insufficient authentication and session managementWeak authentication measures, such as hard-coded or default credentials, can facilitate unauthorized access to critical data.
7. Insecure network architecturePoorly configured network architecture and inadequate segmentation increase the attack surface and allow lateral movement for attackers.
8. Outdated software and patch managementIf regular updates and patches are not conducted, the system could be exposed to vulnerabilities that hackers can exploit.
Train your developers on secure coding practices and regularly conduct code reviews and static code analysis to identify and remediate security flaws in the source code.
2. Implement data minimization and anonymization techniquesAdopt data minimization principles to collect and retain only the minimum necessary data. Data anonymization helps to anonymize sensitive data through tokenization and hashing to reduce exposure in case of a breach.
3. Deploy intrusion detection and prevention systems (IDPS)Install and configure IDPS to monitor network traffic and detect unauthorized access or malicious activities. Integrating IDPS with centralized logging and monitoring systems helps provide comprehensive visibility into security events and incidents.
4. Implement strong access controls and authentication mechanismsImplement centralized identity management solutions to streamline the organization's user authentication and authorization processes.
5. Encrypt sensitive data at rest and transitImplement robust encryption algorithms (eg, AES-256) to encrypt sensitive data stored on servers, databases, and storage devices.
This vulnerability exposes the application to a spectrum of risks, potentially compromising the confidentiality, integrity, and availability of the application.
|
Exploitability |
Easy |
|
Detectability |
Easy |
|
Technical Impact |
Moderate |
|
Business Impact |
Moderate |
Without proper protections like stack canaries or address space layout randomization, hackers can overwrite crucial data, inject malicious code, and gain control of the program’s execution flow.
2. Return-oriented programming (ROP)Insufficient protections, such as a non-executable stack or data execution prevention, make it easier for attackers to construct ROP chains, bypass security mechanisms, and execute arbitrary code.
3. Format string vulnerabilityThe lack of format string protections enables hackers to manipulate memory content, leak sensitive information, or overwrite data.
4. Heap exploitationHeap spraying, double-free vulnerabilities, and/or use-after-free can be leveraged to corrupt heap data structures, manipulate memory allocations, and execute arbitrary code.
5. Integer overflow/underflowWithout checks, attackers can manipulate integer calculations to control program behavior.
6. DLL injectionsHackers can inject rogue DLLs into the process address space without checks, enabling them to hijack program execution.
7. ROP gadgets in code reuse attacksWithout control flow integrity, attacks can bypass control flow restrictions and achieve arbitrary code execution using ROP chains.
It obscures program logic and structure by adding complexity, making reverse engineering and exploitation challenging.
2. Binary hardeningIt applies techniques such as stack canaries, Address Space Layout Randomization (ASLR), Data Execution Prevention (DEP), and control flow integrity.
Common security misconfigurations occur as a result of leaving default settings unchanged. These are considered the top cloud vulnerabilities.
|
Exploitability |
Difficult |
|
Detectability |
Easy |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
Hackers can easily search for devices or systems with default credentials and exploit such devices.
2. Unprotected services and portsHackers can scan for open ports and services using tools like Nmap and exploit them to gain unauthorized access.
3. Improper file permissionsAttackers can upload malicious scripts to compromise the system if a web server is misconfigured to allow read or write access to critical system files.
Utilize centralized configuration management tools to manage and enforce security configurations across multiple systems.
2. Network segmentation and firewallsIsolate critical systems and sensitive data from less secure network parts.
3. Implement the least privilege principleGrant users and processes only the minimum level of access required to keep things running smoothly.
Device file systems are no longer contained within a sandboxed environment, and rooting or jailbreaking often bypasses existing protections. Not storing data properly will open your systems to vulnerabilities.
Insecure data storage vulnerabilities occur when developers assume that malicious actors will not have access to their file systems and sensitive information.
However, filesystems are easily accessible. Poor encryption libraries make it easy for malicious actors to view application data via rooting or jailbreaking techniques.
In mobile development, data leaks are most seen in undocumented or under-documented internal processes, such as:
|
Exploitability |
Easy |
|
Detectability |
Average |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
Hackers exploit insecure data storage by leveraging techniques such as SQL injection, where they insert malicious SQL queries into input fields to manipulate database commands and extract sensitive information.
They can also exploit vulnerabilities in file permissions and encryption weaknesses or bypass access controls to compromise stored data integrity and confidentiality.
This vulnerability can result in weak encryption keys, easily guessable passwords, and/or an inability to implement proper encryption.
|
Exploitability |
Average |
|
Detectability |
Average |
|
Technical Impact |
Severe |
|
Business Impact |
Severe |
Hackers exploit insufficient cryptography vulnerabilities by leveraging weak encryption algorithms, predictable key generation, or flawed implementation. They can intercept and decrypt sensitive data, manipulate transactions, or inject malicious code.
Inadequate cryptographic protocols allow attackers to bypass security measures, gain unauthorized access to systems, and compromise data confidentiality, integrity, and authenticity, posing severe risks to organizations and individuals.
Preventing insufficient cryptography vulnerabilities demands strict adherence to cryptographic best practices.
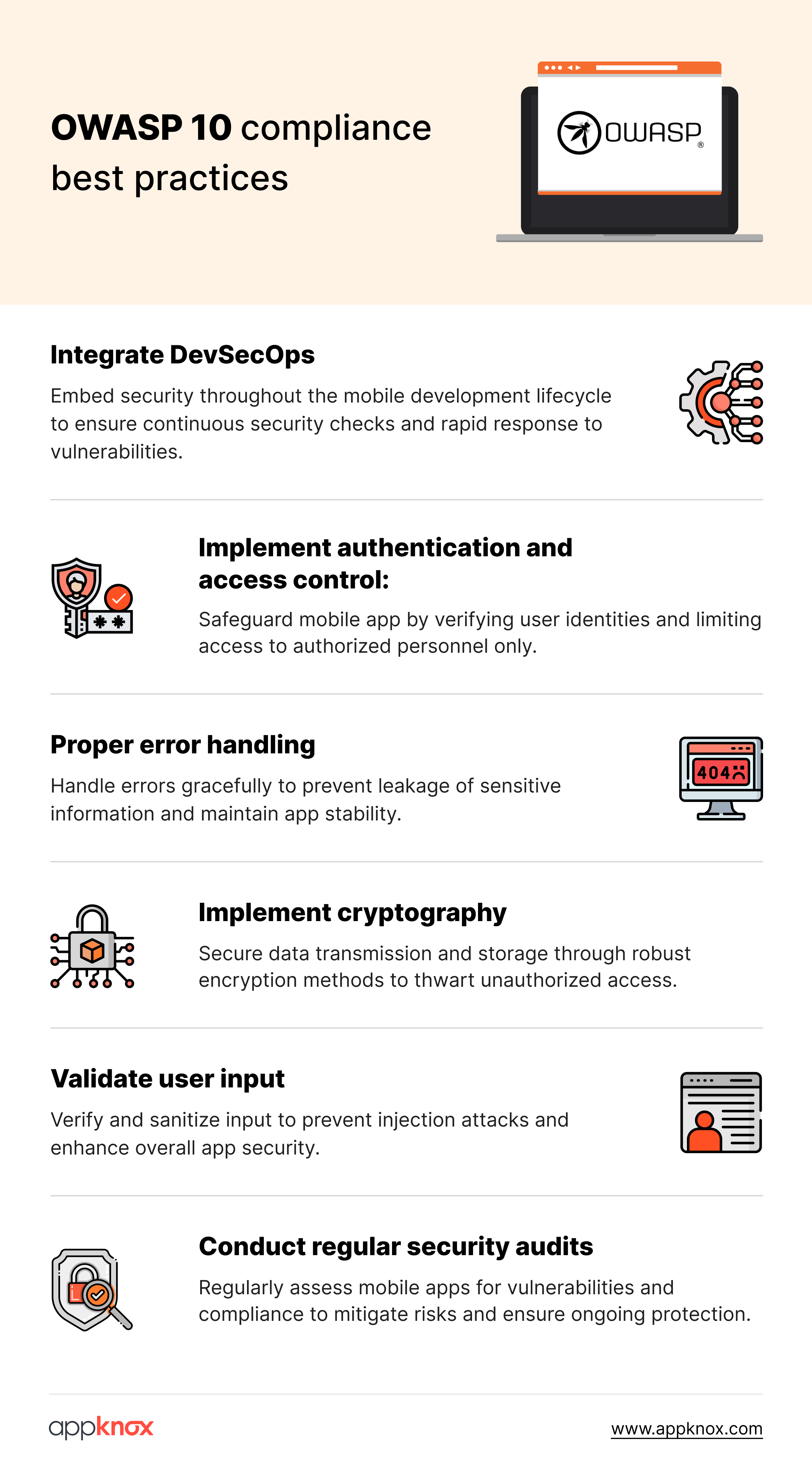
Most organizations understand what the OWASP Mobile Top 10 is. Far fewer know how to operationalize it at scale without slowing down engineering or flooding teams with noise.
The gap isn’t awareness. Its execution.
Auditing mobile apps against OWASP Mobile Top 10 requires more than checking a list of vulnerabilities. Mobile risk is shaped by how code executes on devices, how APIs behave at runtime, and how third-party SDKs interact with user data.
A practical OWASP audit for mobile apps includes:
Static analysis to identify insecure coding patterns, misused cryptography, hardcoded secrets, and unsafe permission usage
Dynamic testing to validate whether weaknesses are actually exploitable at runtime
API-level validation for broken authentication, authorization bypasses, and excessive data exposure
SDK behavior inspection, especially for analytics, ad networks, and social login libraries
What separates mature audits from checkbox exercises is mapping findings directly to OWASP Mobile Top 10 categories, so teams understand which class of risk exists, not just which line of code failed.
This mapping enables security leaders to answer audit questions confidently and developers to resolve issues without ambiguity.
OWASP checks become effective only when they run automatically and consistently.
Manual audits, quarterly reviews, or pre-release fire drills don’t scale with modern mobile delivery. OWASP enforcement must happen where code changes happen, inside CI/CD pipelines.
Mature teams embed OWASP checks by:
Triggering SAST scans on every commit or pull request
Running DAST scans on staging or pre-production builds
Blocking releases when critical OWASP categories are violated
Surfacing results directly in build logs or issue trackers
This approach shifts OWASP compliance from a security task to a development quality gate.
The outcome isn’t slower releases, but fewer late-stage surprises and significantly lower remediation costs.
📌Key takeaway: OWASP Mobile Top 10 only reduces risk when it’s enforced continuously inside development and release workflows.
Detection without prioritization is how vulnerability backlogs grow.
Not every OWASP finding deserves equal attention. High-performing teams prioritize based on real-world risk, not raw severity scores.
Effective prioritization considers:
Exploitability in real execution paths
Exposure in production-facing flows
Sensitivity of impacted data
Business impact, not just technical severity
For example:
A medium-severity issue on an internal test API may be acceptable in the short term
A lower-severity flaw in an authentication or payment flow is not
OWASP categories involving authentication, authorization, and sensitive data handling should always outrank cosmetic or theoretical findings.
This discipline is what prevents teams from fixing “easy” issues while critical risks linger.
SAST and DAST are complementary, and remediation works best when their findings converge.
Static analysis shows where insecure patterns exist. Dynamic testing shows whether those patterns are exploitable.
Mature remediation workflows:
Correlate static and dynamic findings to confirm real risk
Assign issues directly to developers with contextual guidance
Re-run targeted scans to verify fixes
Track recurring issues to prevent regressions
When fixes are validated automatically, OWASP compliance becomes repeatable rather than reactive.
📌Key takeaway: OWASP risk reduces only when teams fix the right issues first and verify that the fixes actually work.
OWASP detection breaks down when tools lack mobile context or operational tuning.
Teams often blame tools when OWASP detection fails. In reality, failures usually stem from misalignment between scanners and mobile behavior.
Common challenges include:
Generic scanners that don’t understand mobile permission models
Excessive false positives from untuned rule sets
Missing coverage for mobile-only flows like OTP, deep links, or device registration
Incomplete visibility into third-party SDK behavior
The solution isn’t “more scanning.” It’s mobile-aware detection, tuned to how apps actually behave on devices and networks.
OWASP maturity isn’t measured by the number of scans run; it’s measured by outcomes over time.
Indicators of a mature OWASP program include:
Fewer recurring OWASP issues across releases
Faster remediation of critical categories
Reduced exposure window for high-risk vulnerabilities
Consistent compliance evidence during audits
Trend-based dashboards help teams move from firefighting to prevention, where OWASP becomes a guardrail, not a bottleneck.
Manually identifying security gaps based on the OWASP list is challenging and time-consuming.
Appknox, an automated vulnerability assessment tool, swiftly detects and tracks potential vulnerabilities, generating detailed CVSS reports. These reports provide actionable remediation notes, enabling security teams to promptly address risks and ensure adherence to the highest security standards.
Our test cases have been mapped to the latest guidelines released by OWASP for mobile application security. This will make it easier for you to match all your compliances.
Furthermore, Appknox’s binary-based SBOM scans your app's files and libraries to build an inventory of all frameworks, libraries, components, and code licenses. This inventory and all vulnerabilities in your supply chain are packaged into an easy-to-read report.
With Appknox’s binary-based SBOM, you can:
You can also easily view all past SBOM analyses, understand how your mobile application’s supply chain security has improved, and analyze any repeat vulnerabilities.
Assessing OWASP compliance requires thorough scrutiny, which manual assessments often overlook. Appknox’s automated vulnerability assessment tool offers a comprehensive view of risks, providing scores after detailed evaluations.
With Appknox, you can now proactively identify application security weaknesses, effectively mitigate potential breaches and data leaks, and safeguard your applications against evolving security threats.
Yes, everyone should focus on OWASP. It provides a holistic list of all types of web and mobile applications’ security risks and vulnerabilities.
OWASP mobile security is a set of practices, guidelines, and tools provided by OWASP that are specifically tailored to address security concerns and threats to mobile applications. It includes
Audit using a combination of static analysis, dynamic testing, API validation, and SDK inspection, mapped directly to OWASP Mobile Top 10 categories for clarity and accountability.
Trigger automated SAST and DAST scans during builds and releases, and enforce security gates for critical OWASP categories to prevent insecure deployments.
To fix vulnerabilities listed in OWASP Mobile Top 10, prioritize by exploitability and business impact. Focus first on authentication and sensitive data flows, and validate fixes by rescanning.
False positives occur when scanners lack mobile context or when rules aren’t tuned to real execution paths. Mobile-aware testing significantly reduces noise.
By running SAST early, validating APIs continuously, reviewing SDK behavior, and embedding OWASP checks into CI/CD workflows, developers can avoid OWASP Mobile Top 10 issues early in the development cycle.
To measure improvement in OWASP security, track reductions in recurring OWASP issues, remediation speed, and the number of critical findings reaching production.

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
