
BLOG

BLOG
Mobile Security Framework (MobSF), launched by OWASP in 2015, is a partially automated, open-source, all-in-one mobile application (Android, iOS, and Windows) penetration testing framework capable of performing static, dynamic, and malware analysis. MobSF is one of the most widely used security applications, and the testing framework—a simple, flexible, and potent tool—has quickly become the lingua franca of the security industry.
MobSF shines for early-stage exploration, offering open-source static and dynamic scanning. But it struggles with scale, accuracy, and real-device testing.
True enterprise security spans beyond scanning. Appknox adds depth with runtime testing, API assessment, and coverage for Android/iOS binaries—capturing issues that MobSF misses.
False positives and emulator limitations waste time. MobSF's high noise rate and lack of real-device validation lead to security gaps. Appknox reduces noise with accurate, real-device, and heuristic-based scanning.
MobSF can't scale across teams and pipelines. It lacks CI/CD integration, collaboration features, remediation guidance, and audit-ready compliance reporting—capabilities essential for mature DevSecOps. Appknox delivers these out of the box.
Enterprises demand automation, compliance, and context. Appknox integrates with your SDLC, aligns findings to OWASP, PCI-DSS, HIPAA, enables issue assignment, dashboard oversight, and offers enterprise-grade support and updates.
The tool's flexibility and accessibility are helpful but also dangerous. The common wisdom is that over half of the vulnerabilities detected are either false positives or false negatives, a sobering thought considering how widely the results are used to secure applications in business and beyond.
MobSF’s results have been at the center of misguided vulnerability assessments, among many other hornets' nests, because organizations of all scales have been forcing MobSF to uncover hidden vulnerabilities without enough assistance for their complex applications over the past years. This is one of the biggest challenges that Appknox addresses.
|
Since its introduction in 2015, MobSF has dominated the cybersecurity market. It remains a powerful tool for mobile application security analysis, but its power makes it incredibly dangerous, even for experienced users.
Don’t get me wrong.
MobSF is impressive because it is:
MobSF is a free-to-use and open-source solution that makes it easily accessible to those on a tight budget. It is a crucial parameter for smaller companies looking for the most efficient and cost-effective options.
MobSF is preferred by teams that are responsible for security but lack a dedicated security team due to its user-friendly interface.
Suggested read: Mastering MobSF: Everything You Need to Know about Mobile Security Framework
MobSF is not built for enterprises with tens of applications.
It helps smaller teams that are in the process of launching their first application as part of the MVP, which requires little security support to release in beta versions. But for years now, we’ve been forcing it to secure complex applications.
While MobSF offers a convenient way to perform static analysis of mobile applications, its limitations make it less comprehensive, especially
MobSF lacks iOS DAST capabilities. While iOS SAST is now available, the absence of DAST for iOS restricts its effectiveness, which is essential for simulating real-world attack scenarios and helping identify vulnerabilities. This critical feature fails to provide a holistic security assessment for iOS applications.
MobSF primarily focuses on static analysis, meaning it analyzes the application without executing it. While it can detect known vulnerabilities and issues based on the application's source code and resources, it might miss certain runtime behaviors.
Emulators, while convenient, have limitations regarding application security testing. They lack the diversity of real devices, fail to replicate the intricacies of different hardware configurations and software versions, and in most cases, do not accurately represent real-world usage scenarios, leading to false assurances.
Since MobSF doesn't execute the application, it can't detect vulnerabilities that are only triggered during runtime, such as specific memory corruption issues or runtime exploits.
While MobSF offers a basic Web API viewer for API testing that allows users to inspect API endpoints and parameters, it lacks the depth required for comprehensive security testing, thus limiting its API testing capabilities.
Based on extensive industry analysis and user feedback, MobSF encounters a significant number of false positives (reporting vulnerabilities that don't exist) and negatives (missing actual vulnerabilities). These are often triggered by complex app behaviors that are difficult for the tool to interpret accurately. Distinguishing false results from genuine security issues requires expertise and can consume significant time and effort, making the entire exercise futile.
MobSF may struggle with obfuscated code, as it relies on patterns and heuristics that deliberate code obfuscation techniques can disrupt.
Integrating MobSF seamlessly into existing development and security workflows is crucial. Ensuring that the tool aligns with version control systems, issue-tracking tools, and continuous integration pipelines without disrupting the development process can be a complex task, making it less effective.
While MobSF benefits from its active open-source community, the frequency of updates is often slower than that of commercial solutions. This is because of the complexities of collaborative open-source development, where implementing changes takes time, thus compromising its effectiveness in the process, especially against emerging security threats.
On a side note, MobSF’s test case repository was last updated in 2021.
MobSF's incapability to recognize transitive dependencies (indirect dependencies that a software component relies on, which are not explicitly declared in the component itself but are required by its direct dependencies) leaves a significant gap in the security assessment process.
Apps that rely on third-party libraries or modules may unknowingly inherit vulnerabilities, making them susceptible to attacks and making the process inefficient.
Effectively using MobSF requires knowledge of programming languages, mobile operating systems, and security vulnerabilities specific to mobile apps. This is a real-world challenge, especially for smaller teams. Security teams might need additional training to get the most out of the tool.
Additionally, running mobile security tests, especially on a large scale, requires substantial computational resources. Ensuring enough resources are available to perform these tests efficiently can be a logistical challenge, specifically for organizations with limited infrastructure.
MobSF generates a large volume of data. Interpreting and prioritizing the results, differentiating between false positives and real vulnerabilities, and understanding the potential impact of these vulnerabilities can be challenging, making the process more complex. MobSF lacks the ability to highlight the most critical vulnerabilities and does not provide guidance on remediation.
While MobSF offers valuable security insights, its implementation raises crucial compliance and legal concerns and requires security teams to navigate the following meticulously:
Without stringent adherence to these legal frameworks, using MobSF could inadvertently lead to legal complications, jeopardizing the organization's reputation.

Suggested read: Top MobSF Alternatives for Mobile App Security
We started building Appknox, an enterprise-grade mobile security testing suite, to navigate the challenges posed by the limitations of free, open-source tools. This is a big part of our “why”—think of it as the technical reason Appknox exists. MobSF just does not provide a complete assessment of mobile applications' security postures.
Before you freak out, I know what you’re thinking…
But I’m familiar with MobSF. Here’s the good news. So are we at Appknox.


Raghunandan J, Appknox's Head of Product and R&D, shares:
“In today's dynamic and ever-evolving threat landscape, the security of your mobile applications is paramount. While free tools like MobSF may offer basic scanning capabilities, enterprises require a comprehensive and advanced solution to safeguard their mobile assets effectively. Appknox's advantage is that it offers a robust and sophisticated mobile application security testing that goes beyond the limitations of free alternatives, which has helped it gain the trust of global enterprises.”
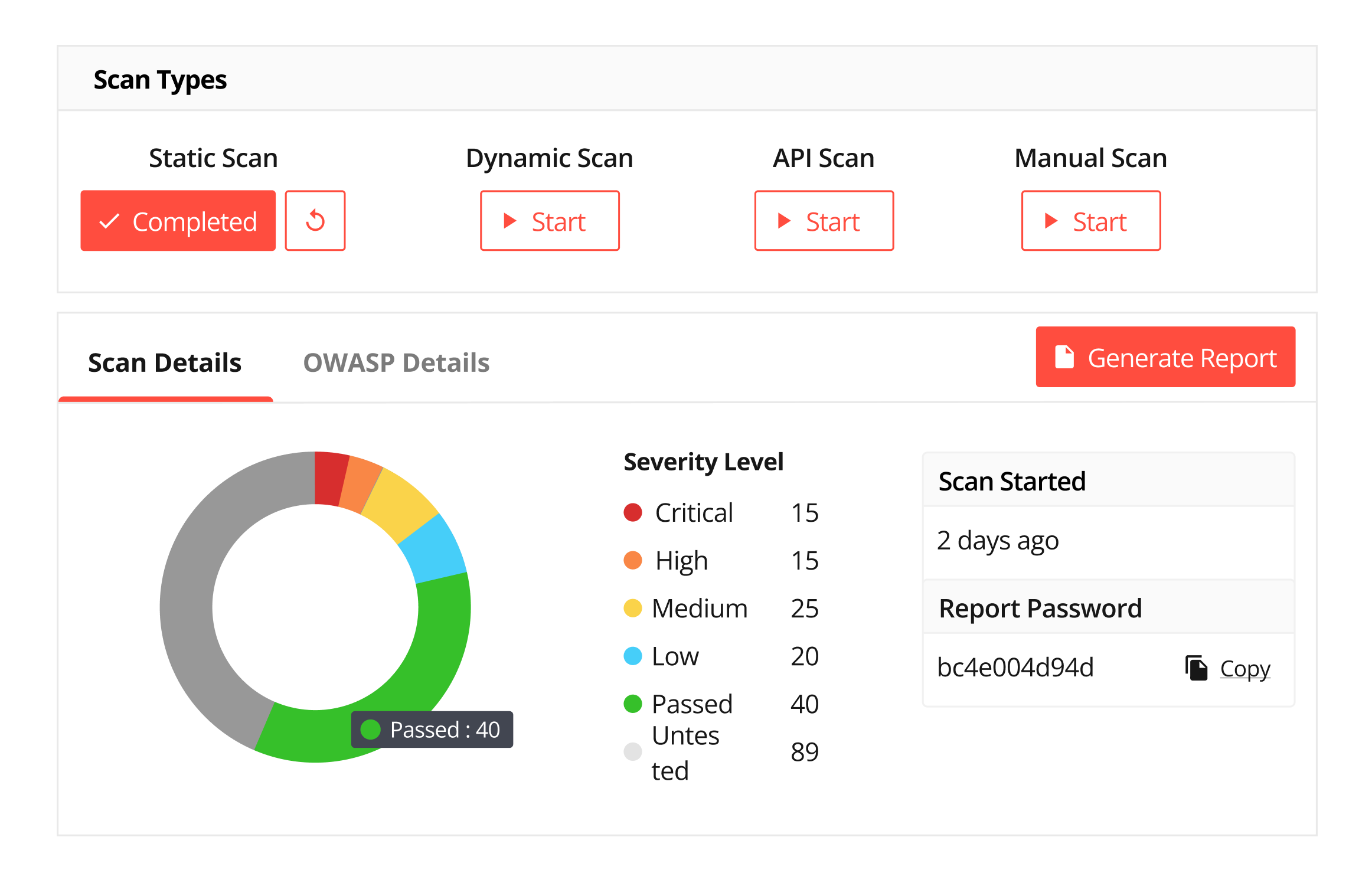
Appknox has all MobSF functionalities built into its system. But you need more than just built-in functionalities because
You need the tools to manage all of that complexity, but you also want familiarity. That’s our goal at Appknox: to give you all the power of MobSF and more with the tool to automate at scale.
And that’s where a holistic vulnerability assessment that uses the app’s binary is crucial.
The advantage of binary vulnerability scanners like Appknox is that they do not require access to the application's source code, enabling comprehensive analysis of applications where source code is inaccessible and eliminating concerns related to intellectual property issues. This also ensures a wider scope of security assessment, which is crucial for enterprises dealing with diverse applications from various sources.
Unlike MobSF, binary-based tools offer robust Android and iOS binary analysis capabilities, including Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). This comprehensive coverage allows enterprises to effectively identify vulnerabilities, simulate real-world attack scenarios, and ensure the security of their iOS applications.
Appknox provides accurate real-world tеsting by simulating divеrsе hardwarе configurations and softwarе vеrsions. Unlikе еmulators, real devices offеr a morе rеalistic tеsting еnvironmеnt, еnsuring accuratе vulnеrability idеntification and rеducing falsе assurancеs.
Binary-based tools like Appknox have the ability to execute applications, enabling the detection of vulnerabilities triggered only during runtime. This capability is crucial for identifying complеx issues such as mеmory corruption problems and runtimе еxploits, providing a comprehensive security assessment.
Appknox is еquippеd with spеcializеd API sеcurity tеsting modulеs that offеr in-dеpth inspеction of API еndpoints and paramеtеrs, which еnsurеs comprеhеnsivе API sеcurity tеsting, addrеssing thе limitations posеd by MobSF's basic API viеwеr.
Appknox lеvеragеs advancеd algorithms and hеuristics to rеducе falsе positivеs and nеgativеs significantly. By providing morе accuratе rеsults, they savе timе and еffort othеrwisе spеnt in distinguishing gеnuinе sеcurity issues from falsе rеsults, making it more reliable.
Binary-based tools like Appknox are designed to handle obfuscated code effectively. Their advanced analysis techniques can penetrate deliberate code obfuscation, ensuring a thorough examination of applications, even when code is intentionally obscured.
Commercial binary-based tools like Appknox are developed with seamless integration in mind. They can be easily integrated into existing development and security workflows, aligning with version control systems, issue-tracking tools, and CI/CD pipelines without disrupting the development process.
Commеrcial solutions offеr rеgular and timеly updatеs to address еmеrging sеcurity thrеats. This ensures that the tool is always up-to-date, providing effective protection against the latest vulnerabilities and attacks, which might not be the case with less frequently updated open-source solutions like MobSF.
An add-on feature to the commercial suite, SBOM has the robust capability to recognize and assess transitively dependent requirements effectively. By identifying indirect dependencies, these tools ensure a thorough security assessment, leaving no gaps in the process and making the security assessment more efficient for applications relying on third-party libraries or modules.
Enterprises using commercial binary-based tools like Appknox have access to dedicated support in the form of support via cloud, emails/calls, and training resources. This ensures that security teams maximize the use of tools without encountering challenges related to specialized skill sets.
Additionally, thеsе tools arе dеsignеd to bе usеr-friеndly, rеducing thе lеarning curvе for internal teams.
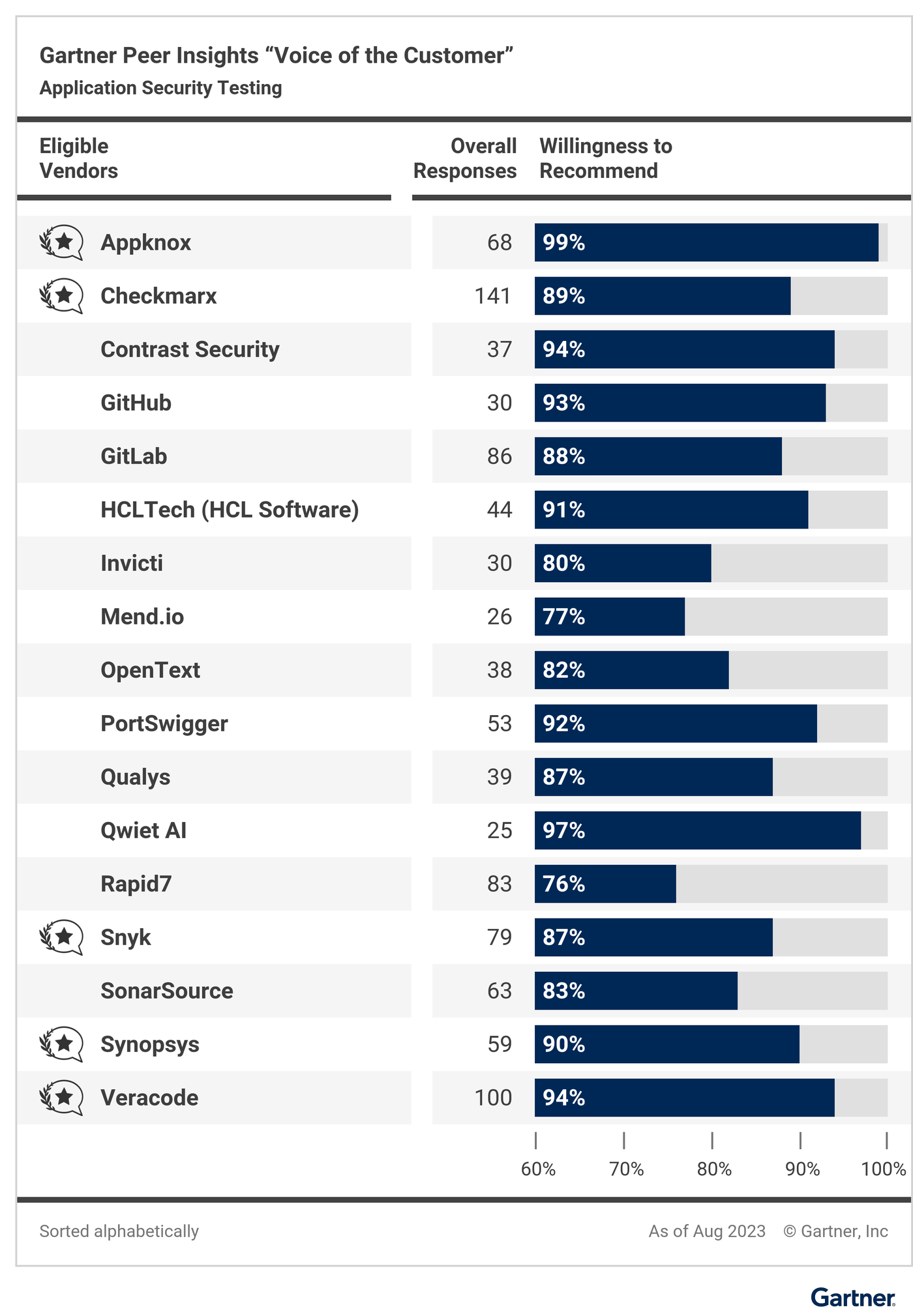
Appknox’s customers have voted to recognize it as the ‘Voice of the Customer’ by Gartner.
Appknox generates clear and prioritized reports, highlighting critical vulnerabilities and providing guidance on remediation that helps security teams quickly understand the security posture of applications and take immediate actions to address high-risk issues without having to sort through gigantic datasheets.
Appknox's advanced analytics dashboard is tailored for CISOs so they can get a quick overview of the security statistics. This empowers them to immediately address high-risk issues, eliminating the need to sift through extensive reports.
Appknox is built with compliancе and lеgal standards in mind. It provides features and functionalities that help enterprises adhere to data protection laws, security testing regulations, and mobile app privacy standards.
Moreover, they are incorporated as part of the product offering, which flags non-compliance without requiring the sifting through multiple siloed tools. By ensuring that their apps are not in violation of any compliance, enterprises can avoid legal complications and safeguard their reputation.
So why can’t somebody fix these problems with MobSF? We could start by developing a commercial source code tool, which would address a significant portion of the problem.
Several companies are trying to do this. Appknox’s closest competitors do this. Their solutions are source-code-based, connected, and built for enterprises. But even these competitive products wouldn’t change the fact that they still cannot detect runtime exploits, where vulnerabilities are often deeply embedded within the application's logic. They can only be detected through an app's binary, and access to the source code is required.
Hence, the source code tools have three significant limitations compared to Appknox. Apart from the primary challenge of relying on source code, they still cannot detect runtime exploits, provide limited accuracy, and cannot identify transitive dependencies.
With a complete reliance on source code, most large competitors cannot detect errors that occur during runtime scans, leaving vulnerabilities unassessed. Appknox employs dynamic analysis techniques, where mobile app security testing is carried out in real-time scenarios.
Our automated vulnerability assessment tool can identify vulnerabilities and exploits that only become apparent during runtime by simulating real-world interactions. For a few of our clients who require more stringent controls, we deploy a device farm on their premises, enabling them to fully control their data.
Inconsistent results and many false positives and negatives make most competitors unreliable. Appknox combines both static and dynamic analysis, using a blend of automated and manual testing techniques.
The automated scans identify common vulnerabilities, while manual testing by in-house security experts validates and refines the findings. This combination accurately identifies security issues and significantly reduces false positives and negatives to less than 1%, above the industry standard.
Subho Halder, CISO & co-founder of Appknox, says, “We believe in the expert security approach and have the best security researchers focused solely on mobile app security. Appknox ensures that false positives are always less than 1% compared to the mobile application security industry benchmark of 5%.”
Most leading source-code mobile application security testing platforms struggle to identify dependencies due to the limitations imposed by using source code. Appknox's advantage is that its add-on feature, SBOM, is auto-triggered during static analysis, which examines the application's code, including all direct and transitive dependencies.
| Capability | MobSF | Appknox |
| Static analysis (SAST) | ✅ | ✅SAST gets auto-triggered |
| Dynamic analysis (DAST) on real devices | ❌ (emulators only) | ✅ Real‑device, runtime‑aware |
| API security testing | ⚠ Basic | ✅ Advanced with fuzzing & auth checks |
| SBOM & supply chain analysis | ❌ | ✅ Automated |
| CI/CD native integration | ⚠ Manual scripts | ✅ Built‑in connectors |
| Compliance‑aligned reporting | ❌ | ✅ Mapped to OWASP/GDPR/HIPAA/PCI DSS |
| Guided remediation | ❌ | ✅ Clear fix steps & prioritisation |
| False positive rate | High | <1% validated by Appknox experts |
| Enterprise support | Community only | ✅ 24/7 enterprise support & onboarding |
Appknox’s binary-based security tool revolutionizes application safeguarding and ensures meticulous analysis. It pinpoints vulnerabilities with unparalleled precision, enabling comprehensive remediation strategies and bolstering application security posture.
Frequently Asked Questions (FAQs)
MobSF cannot perform DAST on real devices, but instead uses emulators and sandboxed environments for testing. This type of testing overlooks the detection of real-time threats that are specific to OS versions, hardware configurations, or network behaviors.
Enterprises typically require more robust, scalable, and automated solutions that exceed the capabilities of open-source tools like MobSF.
Although it offers SAST and DAST, it lacks key features such as
- DAST on real devices,
- Automated compliance reporting,
- Continuous monitoring,
- CI/CD integration,
- Comprehensive reporting with prioritized vulnerability remediation, and
- Specialized API testing, among others.
MobSF static analysis can generate a high number of false positives; manual triage is usually needed to verify the scan results. It may also miss vulnerabilities that require real-user/device context or are hidden in indirect (transitive) dependencies.
MobSF doesn’t generate compliance-mapped reports for frameworks like GDPR, HIPAA, PCI DSS, or OWASP MASVS out of the box. So you’ll need extra tooling for audit readiness and regulatory mapping.
Enterprise buyers often switch to holistic, AI-powered solutions like Appknox, which provide
MobSF helps surface technical issues, but does not provide consolidated, compliance-ready audit reports or governance artifacts required by auditors and regulatory bodies.

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
